The RH-ISAC is officially launching a community Malware Information Sharing Platform (MISP) instance for our core members. By utilizing an open-source threat intelligence platform (TIP) like MISP, we can share, store, enrich, vet, correlate, and analyze our shared intelligence. MISP includes many galaxy clusters containing the MITRE ATT&CK framework, Threat Actors, and Tools, to name a few. These provide added context to our indicators and allow us to describe relations between individual elements.
With MISP being an open-source tool, it is no surprise there are a plethora of integrations for importing or exporting data from MISP to your own security stack at any level, from your SIEM to your SOAR and EDR. For these reasons, we believe MISP is the best choice to allow us to cater to as many of our core members’ threat intelligence sharing and consumption needs as possible.
What is MISP?
The MISP project started in 2011 as CyDefSIG (Cyber Defense Signatures), a personal project of Christophe Vandeplas. It was brought to life due to frustration that too many indicators of compromise (IOCs) were shared by email or PDF documents and were not parsable by automated mechanisms. At some point in 2012, NATO learned of the project and, after looking at other products on the market, deemed the openness of CyDefSIG to be the greatest advantage.
Shortly after, NATO provided developers to work on CyDefSIG and renamed it to Malware Information Sharing Platform. Fast forwarding about 10 years, the name was shortened to just MISP, and the project now includes the core MISP software and a myriad of tools (PyMISP) and formats (core format, MISP taxonomies, warning-lists) to support MISP. It is co-developed by the Computer Incident Response Center Luxembourg (CIRCL), and the project has expanded beyond technical malware IOCs and can also be used to share fraud or vulnerability information.
Why MISP?
The MISP ecosystem is all about accessibility and interoperability. The data formats and API are completely open standards, and CIRCL provides extensive documentation for the platform. The software is open source and what you see is what you get. There is no hidden or premium functionality. If you don’t see something in the platform you want or need, you can customize or extend the software by contributing to the project or putting in a feature request on the project’s GitHub page. Most of us know the pain of having a lot of data and not being able to use it because it’s too much work. One of the primary goals of MISP is to simplify this process and enable you to use your data. Storing, using, and sharing information about threats should not be difficult, and MISP is there to help you get the most out of your data without unmanageable complexity.
Thanks to MISP, you can store IOCs in a structured manner and truly leverage the value of your data in an automated fashion without extended effort. True threat intelligence is more than just indicators of compromise. MISP provides metadata tagging, feeds, visualization, and even allows you to integrate easily with other tools for further analysis thanks to its open protocols and data formats. Seeing helps understanding, and MISP comes with many visualization options to aid in helping analysts find the answers they are looking for. MISP gives you outstanding opportunities to aggregate threat information and take the process of trying to understand how all this data fits together by telling a broader story.
Sharing is caring and vital to the fast and effective detection of attacks. Often, similar organizations are targeted by the same threat actor, whether in the same or different campaigns. MISP makes it easier for you and your trusted partners to share and collaborate on data. Sharing also enables collaborative analysis that can help prevent you from doing the work someone else already did before.
Indicator Enrichment and Vetting
All IOCs shared by core members are automatically enriched using RH-ISAC’s PyOTI (Python Open Threat Intelligence), and appropriate enrichment tags are added to each indicator. PyOTI is an API framework to easily query threat intelligence APIs to get fast, accurate, and consistent enrichment data to provide added context to IOCs.
RH-ISAC tries to ensure that indicators tagged as vetted are high fidelity, have known signatures or known malicious, with low false positive rate. All enriched indicators are tagged using our custom PyOTI MISP taxonomy. Taxonomy tags are expressed as machine tags. Machine tags are often called triple tags due to their format and are composed of a namespace, a predicate, and a value (e.g. namespace:predicate=”value”). This allows an analyst to quickly determine PyOTI as the origin of the tag (namespace), the service or API used for enrichment (predicate), and the outcome of that enrichment (value).
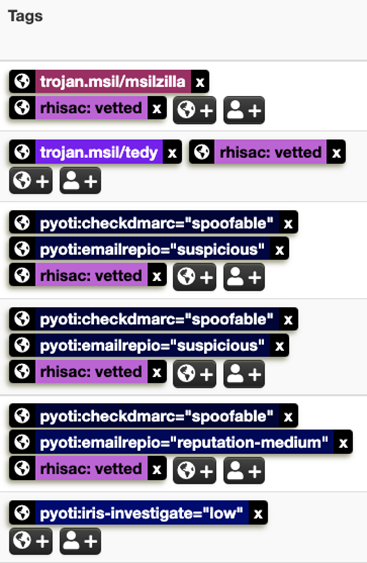
The list of PyOTI taxonomy tags and their definitions can be found in the PyOTI GitHub repository. Users should take care not to confuse enrichment tags as vetted tags. Enrichment tags do not mean an indicator is vetted. The RH-ISAC utilizes a separate, dedicated tag to identify vetted indicators within MISP, such as “rhisac: vetted”.
A Galaxy of Information
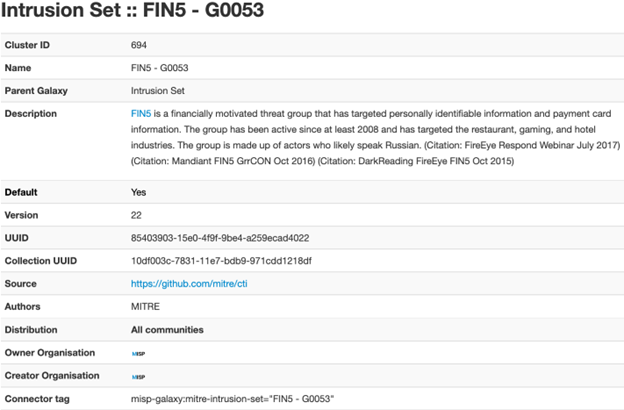
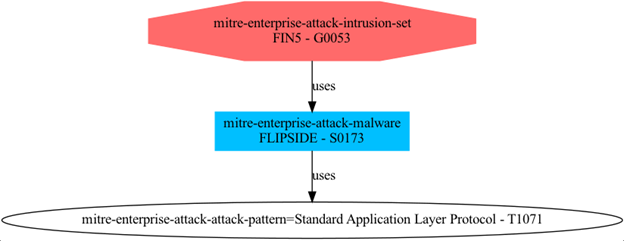
MISP galaxies are a simple method to express a large object, called a cluster, that can be attached directly to MISP events or attributes. Clusters can be composed of one or more elements, and elements are expressed as key-value pairs that can be used as-is or as a common knowledge base. There are several default knowledge bases available within MISP, such as the MITRE ATT&CK framework, Threat Actors, and Tools. These clusters can be overwritten, replaced, updated, forked, and shared as you wish. Galaxy clusters can be used to describe relations between the individual elements in a MISP event, to link together threat actor group synonyms, or mapping MITRE tactics, techniques, and procedures to a specific threat actor. The RH-ISAC will make use of the MISP galaxy clusters by tagging events when the intelligence is shared with attribution provided either by a core member or RH-ISAC’s own research.
Automation and Integrations
Getting data out of MISP and into your security stack can be one of the most challenging parts of integrating a new tool. RH-ISAC’s security integrations team is here to make things a little bit easier. The team maintains a GitHub repository to host integration scripts for our members. At the time of this blog post, we have two types of integration scripts, application-specific integrations and generic scripts to output IOCs to human and machine-readable files. Currently, the application-specific integrations support CrowdStrike Falcon, Microsoft Graph API Security Products (Azure/Microsoft Sentinel and Defender ATP/Defender for Business), and Splunk (and Splunk ES). In addition to those integrations, MISP has an ever-growing list of third-party integrations maintained by both CIRCL and security product vendors. These integrations cover products across the security stack from SIEM to SOAR to mail gateways.
The Art of Information Sharing
What sort of information should go into the event? What should be the category and type of a C2 IP? Learning how to use any new platform can be overwhelming at times.

To relieve this, we have provided our own custom sharing templates that use simple forms for users to aid in populating events to share indicators. Using the RH-ISAC templates helps to remove the guessing and enables analysts to share not only quickly, but efficiently. We currently offer three sharing templates: Credential Harvester, Malware Phishing, and Non-Phishing Malware. However, adding additional templates is quite simple within MISP, and if you have ideas or use cases for new templates, please let us know.
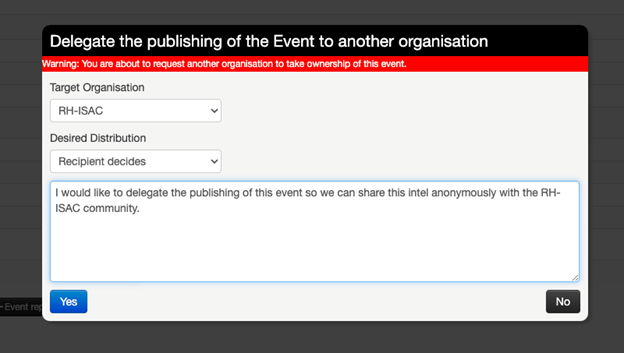
Sharing threat intelligence quickly could be the difference between detecting and alerting on an emerging threat or needing to respond to an incident. Maybe you have been in a situation where you observed a new threat but didn’t feel comfortable being identified as the source of the intelligence. MISP has functionality to delegate the publication of an event which completely removes the binding between the information shared and the organization which shared it. Delegated sharing is the officially supported way to share threat intelligence anonymously with the RH-ISAC community. It allows an analyst to create an event and fill in the context as they normally would, but then publish the event under the RH-ISAC organization without attribution to them or their organization.
MISP’s core functionality is sharing where everyone can be a consumer and/or a contributor/producer. One of the best features of MISP is synchronization (sync). This allows you to directly connect two MISP instances and automatically pull information that meets certain criteria. If a core member maintained their own MISP instance, they could set up a sync to automatically pull over all the indicators inside of the RH-ISAC community instance that have a certain tag, like “rh-isac: vetted”.
MISP sync can be used to both pull and push MISP events, which allows core members to push information back to the RH-ISAC community instance. When an analyst finishes an investigation and wants to provide additional context on an indicator of compromise that came from the RH-ISAC, they can add those attributes to the relevant event, then push them back. With either a push or a pull sync, the transfer of information is automatic, which allows analysts more time to focus on analysis instead of spending time struggling through different processes to share that intelligence with the community.
Conclusion
By using MISP, we will be able to take our sharing community to the next level by moving beyond sharing just indicators of compromise and shift towards sharing true threat intelligence. We can increase the timeliness of threat intelligence sharing exponentially by setting up automation in the form of integrations to a SIEM or SOAR platform or by leveraging MISP to MISP sync connections. Additionally, we’re continuing to develop and update detailed documentation of our MISP instance and the integrations surrounding it to ensure that members can get the most out of the threat intelligence they share and consume.
It may sound a bit cliché, but if you see something, say something by sharing the intelligence with the community. Chances are, if you are seeing a certain threat or phishing campaign, then other members are too! Take advantage of the delegated sharing if you want to share something but want to maintain you or your organization’s anonymity.



