Reports & Documents
RH-ISAC members have exclusive access to a wide array of cyber intelligence reports and resources. See examples of past reports below.
Industry Reports & Documents
CISO Benchmark
Annual benchmark report with data about budgets, personnel, and priorities for InfoSec teams
Industry Insights
Analysis of the Verizon DBIR report as it relates to the retail and hospitality sectors
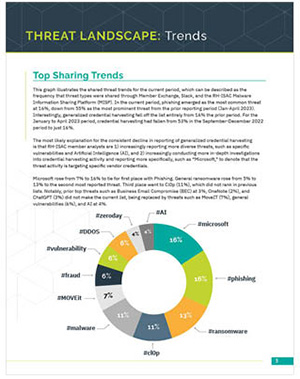
Holiday Threat Trends
Analysis of the top cyber threats facing the retail and hospitality sectors for the holiday season
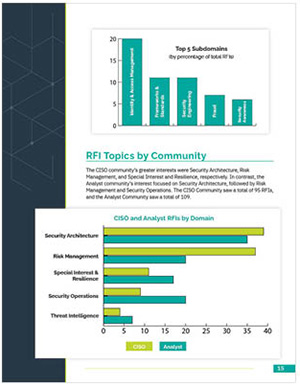
Intelligence Summary
Analysis of the RH-ISAC community’s intelligence-sharing output over a three-month period
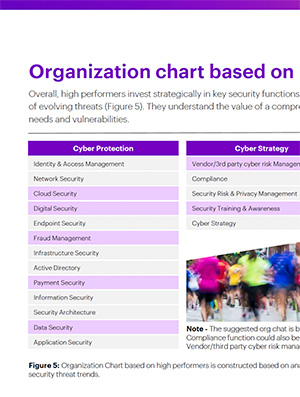
Org Chart Benchmark
Analysis of infosec team organizational charts and staffing priorities
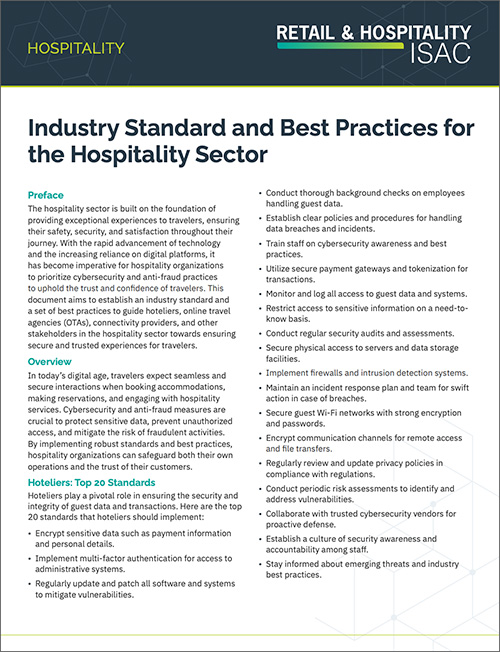
Hospitality Standards & Best Practices
Outline of critical cybersecurity controls for hospitality sector
Retail Fraud Taxonomy
Knowledge base of retail fraud and abuse techniques and related countermeasures
RH-ISAC Documents & Reports
RH-ISAC Membership Overview
An overview of the benefits of joining RH-ISAC as a Core Member
Frequently Asked Questions
Answers to commonly asked questions about RH-ISAC membership
Information Sharing and Transparency
Overview of legal protections for cybersecurity information sharing
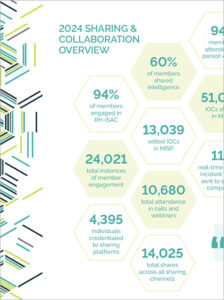
RH-ISAC Year in Review Report
A look back at the key activities and sharing statistics
Join RH-ISAC
Gain access to a wide array of cyber intelligence reports and resources, available exclusively to RH-ISAC members.