Account Takeover (ATO) remains a persistent challenge in retail and hospitality, with attackers continuously refining their techniques. Over the past 18 months, 6.2 million accounts have been compromised – including 55,000 in the last month alone.
Despite advancements in security, automated bot-fueled attacks continue to bypass traditional defenses, costing businesses billions in fraud-related losses and eroding customer trust.
To better understand how these threat actors operate, Kasada’s Threat Intelligence Team infiltrated 22 professional credential-stuffing groups. What we uncovered confirms that these operations have evolved into highly organized, scalable, and efficient businesses.
The Credential Stuffing Economy
Credential stuffing – which leads to automated account takeovers – has matured into a well-oiled machine, with cybercriminals leveraging automation to attack companies at scale.
Key Findings from Kasada’s Threat Intelligence Team:
- Credential stuffing groups operate like full-fledged businesses. Organized operations are complete with customer support, tutorials, and even service-level agreements guaranteeing successful account takeovers.
- Automated attacks are more dynamic and faster than ever. Tools like OpenBullet and SilverBullet provide pre-configured scripts, enabling credential stuffing attacks to launch in minutes.
- Stolen credentials are strategically packaged, targeting specific companies and verticals. Dark web marketplaces and Telegram channels offer bulk credential lists, often categorized by targeted companies in specific industries in retail and hospitality like quick service restaurants and airlines.
- Fraud-as-a-Service is thriving. Attackers now specialize in different stages of the fraud process, offering paid services that make ATO and downstream fraud easier to execute and scale.
Retail & Hospitality: A Prime Target for Credential Stuffing & ATO Attacks
Retail and hospitality brands remain among the most lucrative targets for credential stuffing and ATO attacks. Attack patterns in these industries highlight the persistent and evolving nature of threats. For example:
- Retail/eCommerce and Food & Beverage saw a steady rise in attacks from March to August.
- Travel/Hospitality experienced a surge from January to May before stabilizing.
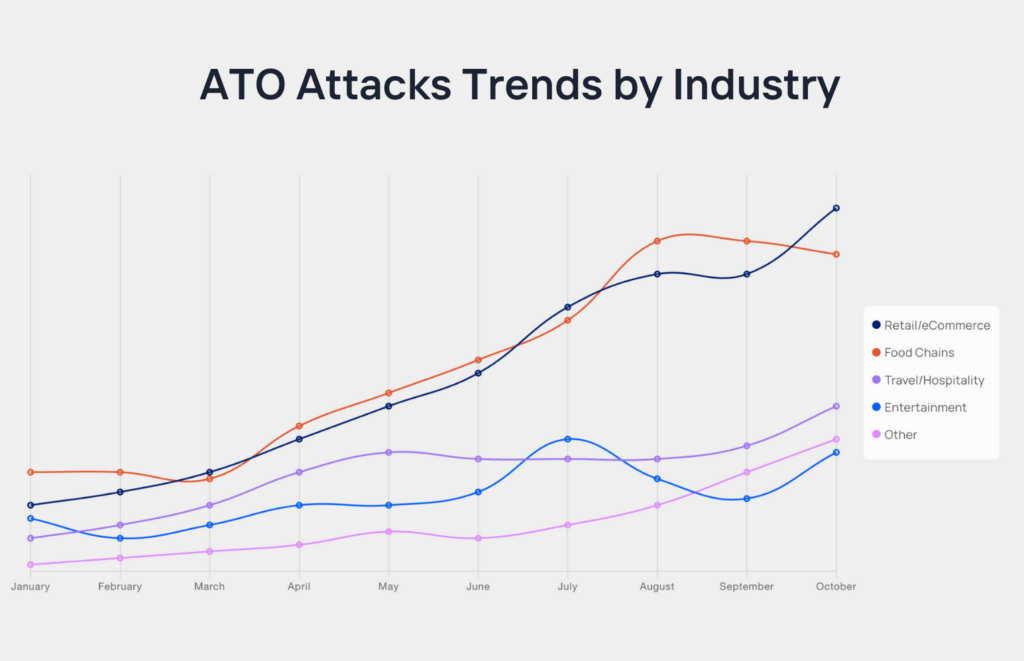
These fluctuations underscore attackers’ adaptability and the constant risk to businesses handling high-value customer data.
Bad actors are drawn to these industries due to the wealth of stored payment information, loyalty points, and reservation systems. Stolen accounts are either resold or used for direct fraud – leading to unauthorized purchases, reward point theft, and illicit bookings.
As attackers refine their tactics, businesses must move beyond reactive defenses and adopt proactive security strategies to safeguard revenue and customer trust.
Why Traditional Security Defenses Are Failing
Many security teams rely on traditional controls like bot detection and MFA. However, these solutions are increasingly bypassed, leaving businesses exposed. The real issue? Automation.
Credential stuffing thrives on automated requests that test stolen credentials across multiple sites. Once a valid login is found, attackers monetize the account through resale or fraud.
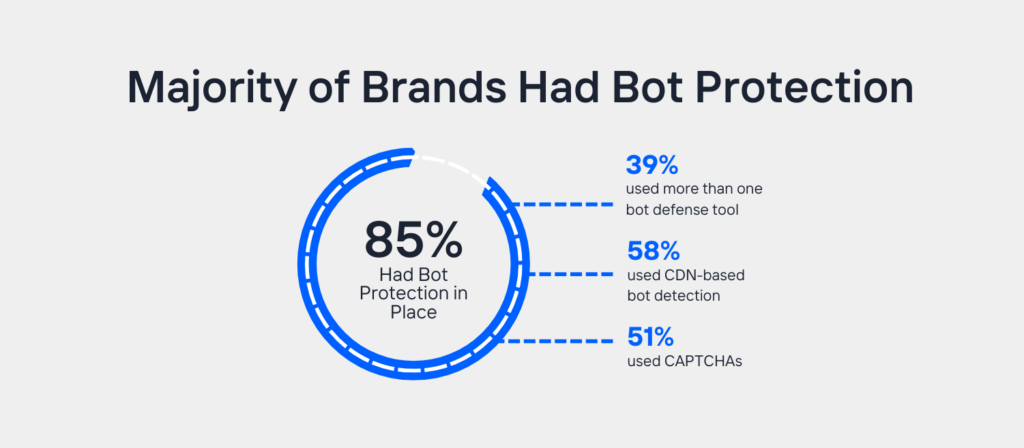
Our research found that 85% of targeted companies had bot detection, yet attackers still bypassed it. In addition:
- 39% used multiple bot detection tools.
- 58% relied on CDN-based bot mitigation.
- 51% used CAPTCHA-based defenses.
Why are these controls failing? 65% of bots used in credential stuffing attacks are now sophisticated, leveraging AI-driven solver services and residential proxies to evade detection.
Retailers, hospitality providers, and travel companies must move beyond outdated defenses and adopt adaptive bot mitigation that evolves alongside threats.
A New Strategy: Stopping ATO Before It Starts
A paradigm shift is needed. Instead of treating ATO as an authentication problem, we must recognize it as an automation problem.
Here are 7 actionable steps for companies in the retail and hospitality industry to disrupt credential stuffing at its core::
- Rethink the True Cost of ATO
- Beyond direct fraud losses, account for chargebacks, customer churn, and security expenses.
- Quantify the combined impact – from fraud and chargebacks to customer support, goodwill gestures, internal ticketing, incident response, and loyalty program costs – to fully grasp how stolen customer accounts affect your bottom line.
- Break Down Silos
- Security, fraud, and customer support teams must collaborate. By sharing intelligence on bot activity and loss signals, organizations can forge joint solutions that address the multifaceted nature of ATO.
- Consider creating fraud fusion centers where cross-functional teams to facilitate sharing insights and rapid response to emerging threats.
- Understand Your Attack Surface
- ATO isn’t limited to the login page. Examine all potential access points – home pages, checkout flows, account pages, and modals – to ensure that every avenue for login is fortified against abuse.
- Implement Business Logic Protections
- Adjust business processes to mitigate risk. For example, reset stored payment methods after an email change or require customers to re-validate their stored credit cards following significant account updates.
- Monitor the Dark Web and Understand Your Adversary
- Stay ahead of threats by tracking dark web marketplaces and hacker forums. Early detection of stolen credentials can help preempt their exploitation.
- Track credential dumps and breach forums to anticipate attacks. Integrate intelligence into technology to prevent the use of known compromised credentials.
- Use MFA as Step-Up Authentication Only
- Rather than requiring one-time passwords (OTPs) for every action, which frustrates users and increases SMS carrier costs, employ MFA selectively as a step-up measure when suspicious activity is detected.
- Continually Educate and Collaborate
- Invest in ongoing training for your teams and engage with industry information sharing groups such as RH-ISAC.
- Continuous education and collaboration ensure that your defenses evolve in step with emerging attack methods.
The Bottom Line: Retail & Hospitality Must Evolve
Adversaries are evolving rapidly, and outdated defenses can’t keep up. With credential-stuffing groups becoming increasingly coordinated and advanced, companies must shift left in their security strategies – stopping automated attacks before they lead to full-scale ATO incidents.
This approach proactively identifies and stops automation before it can compromise customer accounts, providing protection that is both effective and cost-efficient without sacrificing user experience.
Want to Learn More?
📌 Get the 2025 Kasada Account Takeover Attack Trends Report
🖥️ Webinar Recording: Watch LSA, RH-ISAC, and Kasada reveal insights from infiltrating 22 credential stuffing crime groups.



