SaaS Security: A Changing Model of Cybersecurity
Businesses today commonly employ hundreds of individual SaaS applications for a variety of specific functions, but the majority of sensitive data is typically entrusted to a small set of foundational enterprise applications. Security leaders are well aware that the transition to SaaS has prompted increased targeting by bad actors and recognize that SaaS cybersecurity is more important than ever—but the way teams are thinking about and equipped to protect SaaS needs a new approach.
For years, security teams focused on securing things: endpoints, servers, and networks, for example. To help achieve this, endpoint detection and response (EDR) solutions were used to monitor and mitigate threats residing on user devices and servers, while network detection and response (NDR) tools protected the network.
Although the transition to cloud-based applications has fundamentally changed the coverage model for application security, many teams are still intently focused on securing the clients and their connections while overlooking other critical components of SaaS. Better SaaS security requires a new approach and a different way of thinking uniquely designed around the architecture of cloud-based applications—a holistic solution that extends the principles of zero trust to SaaS.
The Core Components of SaaS
To better understand how to approach SaaS security, you should first consider the three core components of an application’s architecture:
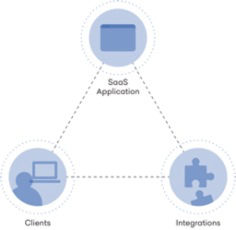
- The client connection to the application
- The SaaS application itself
- Other applications integrating with it
A holistic approach to SaaS cybersecurity is predicated on the fact that each of these components can be a source of risk to the entire application. In addition, with applications so tightly connected to each other, a breach originating at any one of these points can threaten your wider SaaS environment. With this understanding, a security team can begin to evaluate risk end-to-end, ascertain the impact of a threat, and make informed decisions to better protect their business-critical applications.
Securing the Client Connection
Monitoring the client connections to your SaaS environment is essential. Your security team needs to understand the authentication, privileges, and actions of your users within and across business-critical applications to define the scope of each user’s risk. This data needs to be aggregated and normalized from every application into a single, easily understood format in order to be readily accessible to your security team. This is absolutely key to extending the zero trust model of “never trust, always verify” beyond the identity providers and into the SaaS applications themselves.
Securing the Application
The SaaS applications that are core to your business are inherently unique and complex systems with the intricacies and high-level functions that one might expect from an operating system. Securing these applications requires a deep understanding of each platform, its structural vulnerabilities, and issues specific to your own environment. Continuous monitoring of the application security posture is critical here—this includes both application configurations and the privileges granted to your users.
SaaS security posture management (SSPM) shouldn’t just mean knowing the state of your controls and privileges, but actually monitoring the activities associated with them to detect lapses or identify issues that aren’t available via the application API.
Securing the Integrations
SaaS users and administrators integrate third-party applications into core applications in order to expand functionality, automate workflows, communicate with other services, or even play their favorite games. Once authorized, these connections maintain their permissions and access to the core application persistently—a vulnerability that can present a serious security risk if left unchecked. Even vetted third-party applications can be compromised by an attacker, providing a backdoor into core applications. Without continuous monitoring and threat detection to verify the integrations, they fall outside of the zero-trust framework.
Obsidian’s Comprehensive Approach
Today’s SaaS environments are fundamentally complex, interconnected webs of users connecting to applications, each of which has its own unique configurations, privilege models, and integrations with a variety of other services. This is why it’s paramount to find solutions that take a holistic approach to SaaS security and incorporate applications into the zero trust model.
Obsidian Security is the first truly comprehensive SaaS cybersecurity solution built with a deeper understanding of your business-critical applications. Our holistic approach starts with a consolidated understanding of the three core components of SaaS—the client connections, the applications, and the integrations—in order to inform our threat detections and contextualize our posture hardening recommendations. This understanding also enables Obsidian to take zero trust beyond the identity provider and validate components within SaaS itself.
To learn more about how Obsidian closes the gaps in your security stack, read the Obsidian Security Solution Overview.
