Account takeover (ATO) and fake account generation attacks have become wildly successful in recent years, so much so that the FBI’s Cyber Division issued a recent warning to businesses about the growing threat of automated attacks.
To better understand the current landscape as it pertains to retailers, Kasada analyzed the National Retail Federation’s (NRF) Top 100 Retailers list and found that 52% had existing accounts for sale on criminal underground marketplaces. What is more shocking is that over two-thirds of these organizations already have a bot solution in place.
Kasada’s threat intelligence team monitors several online marketplaces and botting forums where accounts, credentials, bypasses, methods to get free upgrades or items, and more, are listed for sale. Accounts often contain payment methods, gift cards, rewards cards, and loyalty points.
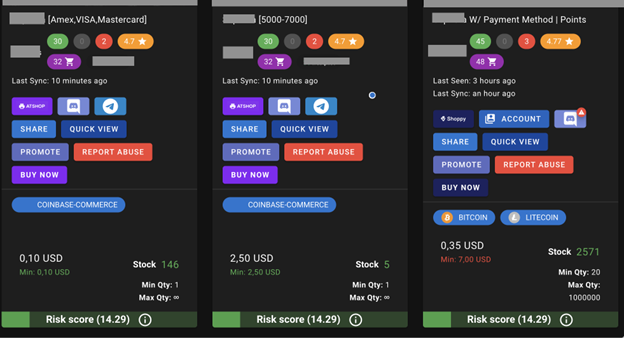
In observing these marketplaces, there’s no denying how lucrative using bots to exploit businesses has become.
To maximize their efforts, adversaries often deploy ATO attacks against retailers or hospitality organizations where accounts possess payment methods (credit or debit cards, store cards, gift cards), reward points, or personal information. Threat actors also create fake accounts at these organizations, as it offers scalable ways to purchase hype products, enter contests, launder money, or commit fraud.
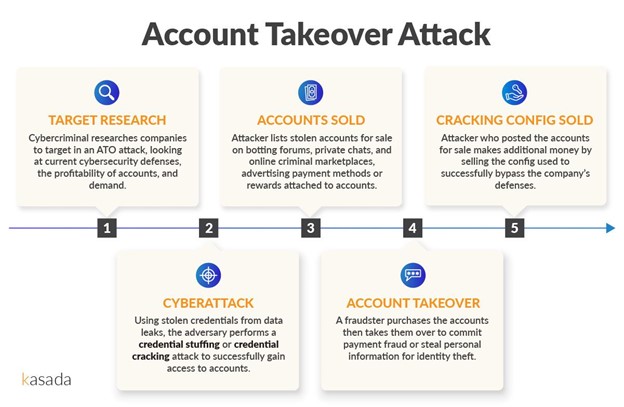
To successfully perform ATO or create fake accounts, fraudsters use automated attacks like credential stuffing or credential cracking.
- Credential Stuffing: A brute force attack that allows bot operators to test large numbers of previously breached credentials from other platforms at once to gain access to a user’s account fraudulently. Breached credential lists are commonly obtained or bought from cracking forums or the dark web and contain email, username, and password combinations. This type of attack is one of the most common automated threats retailers and hospitality organizations face.
- Credential Cracking: A brute force attack that tests random values for usernames and/or passwords to identify valid login credentials.
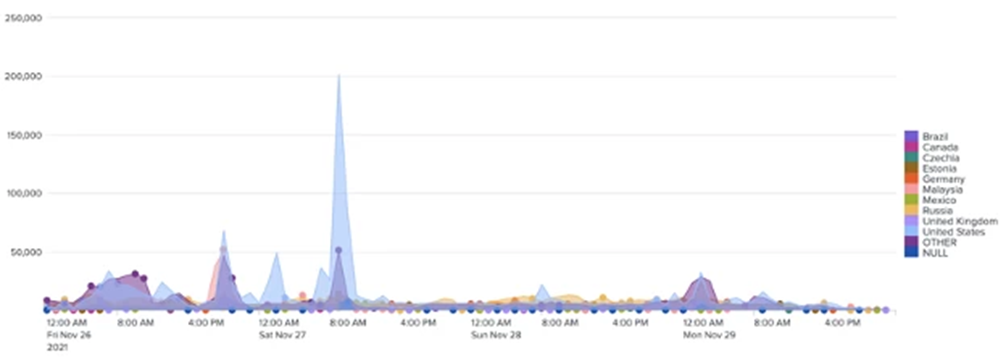
Credential stuffing and cracking attacks become even more prevalent during the upcoming holidays. These automated login attempts are most likely conducted to sell stolen account details, which are used for washing credit cards, draining loyalty and reward points, and committing other forms of fraudulent activity. During the period between last year’s (2021) period between Black Friday and Cyber Monday, the Kasada Threat Intelligence Team has identified a 10x increase in malicious login attempts due to credential stuffing compared to the prior weeks in November.
While these threats are always prevalent for retail and hospitality organizations, times of heightened traffic increase the importance of detecting and stopping bad actors so real customers are not only protected but can successfully access the goods and services they are searching for.
Successful attacks can result in fraudulent purchases, financial loss, system downtime, remediation expenses, and, often the most difficult to remedy, reputational damage. According to Kasada’s recent State of Bot Mitigation report, 69% of organizations surveyed lost over 6% of their revenue due to account fraud, while 40% lost over 10% due to account fraud.
So how exactly are these attacks getting through if 82% of the organizations on the NRF Top 100 list already had some form of bot detection in place?
The FBI’s warning specifically calls out proxies and configurations, but these tools are just a few of the tricks attackers use. Open-sourced tools and solver services are also to blame for enabling bots to carry out attacks. It’s crucial for retail and hospitality organizations to understand the wide range of resources fraudsters use today.
Tools and Tactics Used in ATO and Fake Account Attacks:
- Proxy Networks: Adversaries use residential proxy networks, such as Luminati (now Bright Data), to look like legitimate users when applying their scripts to conduct automated attacks. These proxy networks allow bad actors to distribute their traffic among numerous innocuous endpoints and remain evasive of IP activity and reputation-based countermeasures.
- Open-Source Tools: Open-source web testing tools, including Puppeteer, Playwright, and Selenium, are used to automate scripts to look and act like humans.
- Disguised Behavior: Some bot management defenses make a decision on whether a user is human or not by looking at patterned behaviors like mouse movements, clicks, and days/times of the week people in that time zone would be awake. Bot operators build these behaviors and timeframes into their automation to try and simulate a human’s behaviors.
- Configurations (configs): Proven methods to bypass a specific organization’s bot defense that operators sell and resell to each other in underground botting communities. These bypasses often involve automation tools like OpenBullet to allow fraudsters to launch ATO attacks through credential stuffing. Sometimes configs are sold for a premium price that allows exclusive access to the config for a set period of time before it’s opened up to the rest of the botting community.
- Solver Services: Modern problems require modern solutions. As bot management solutions have gained popularity, a specialized industry has developed to attack, solve, or bypass anti-bot countermeasures. These advanced developers offer their bypass-as-a-service through simple APIs at very affordable rates, allowing low-skilled bot actors to continue their attacks unimpeded.
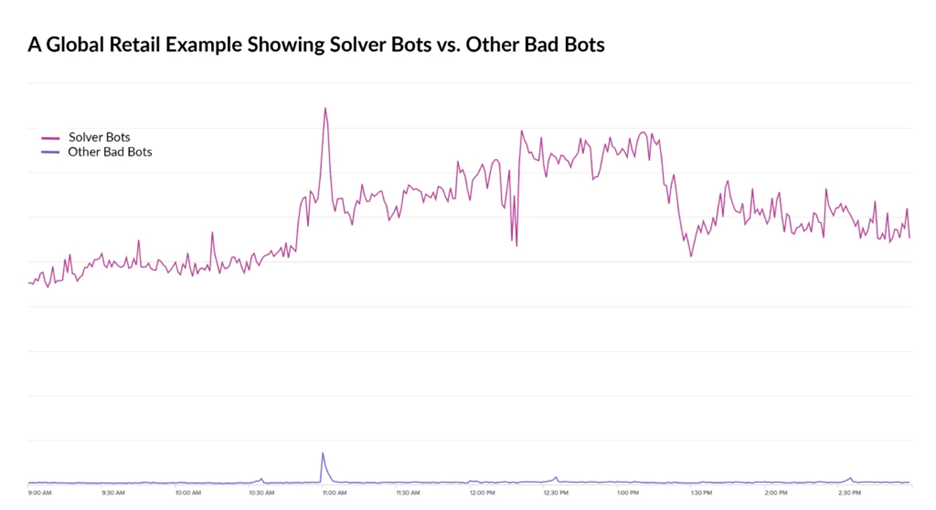
The ways in which bot operators avoid detection and bypass bot defenses are ever-changing, and as the bot communities grow, they will continue to evolve and crowdsource new methods. They’re fast, agile, and highly motivated. Defense updates may take months for traditional bot management organizations to develop, but bot operators retool or reverse engineer those updates in mere hours.
What can be done to stay ahead?
The key to staying ahead of the bot ecosystem is agility. Updates in defenses must happen quickly and require organizations to anticipate attacks before they happen.
Organizations should look for solutions that don’t rely on IP address targeting, behavioral analytics, or device fingerprinting alone. The FBI also included a warning on using CAPTCHAs stating, “Do not rely solely on CAPTCHA to defend against credential stuffing and other automated attacks. CAPTCHAs may help deter account cracking but can also be easily defeated using CAPTCHA solving services.” Your organization’s tactics should evolve as quickly, if not faster, than the adversaries e-commerce organizations need to defend against.
To learn more about the use of bots in fraud and the rise of solver services, check out Kasada’s recent RH-ISAC podcast episode, Getting Started with MISP & Commercialization of Bots in Fraud. To learn more about bot protection for retail and hospitality, visit Kasada.io.

