This article is a repost from SecurityAdvisor

The same way consumers are trying to find the perfect gifts for friends and family this holiday season, hackers are stuffing inboxes with high volumes of spam and phishing, hoping to find vulnerable employees that are susceptible to attacks.
The COVID-19 pandemic has ushered in the work-from-home era where users have increased their screen time yet are prone to more distractions and higher levels of anxiety. According to a recent Google report, hackers have taken advantage over the last several months, delivering more than 240 million daily spam messages related to COVID-19 and at least 18 million daily phishing and malware emails.
This context is important to understanding that this year’s holiday shopper is not only overwhelmed by everyday responsibilities, but also the influx of information on their computers and mobile devices. Not to mention, the pressure time can place on getting gifts under the tree and meals on the table. It’s no surprise that holiday-related phishing schemes are on the rise.
This is especially relevant for retail customers looking for online bargains and fast contactless delivery. According to a new Check Point Software report, phishing emails have increased by more than 13 times in the last six weeks. Currently, one in every 826 emails delivered is a phishing attempt, compared to less than one in 11,000 at the start of October.
In this article, we will explore how hackers are using cognitive bias techniques to target employees with high volumes of spam and phishing, based on their roles in the organization; as well as key suggestions for engaging end-users so they can identify and report suspicious emails.
Social Engineering Tactics: Taking Advantage of Trusted Brands
For RH-ISAC members, securing corporate and customer data, as well as their organization’s brand reputation are top priorities. And yet, hackers continue to launch specialized attacks that target employees – why? Humans can be manipulated, and when their innermost hopes, fears, and biases are tapped into, hackers have a better chance of accessing the data they’re looking for.
According to SecurityAdvisor’s proprietary research, hackers leverage specific cognitive biases, or an individual’s “subjective reality” that deviates from an otherwise objective norm of rational judgement. How individuals construct their reality can influence their behavior in the world, and hackers are taking it to the next level, enticing them to click on risky links and share sensitive data using a number of social engineering tactics like fake coupons (hyperbolic discounting) and fake messages from their managers (authority bias).
To understand how these social engineering tactics work, SecurityAdvisor assessed more than 500,000 data points from real world situations to see how employees were falling for these schemes and making mistakes. Each data point was mapped to one or more of the inferred biases. The chart below illustrates the top nine cognitive biases hackers use.

Hackers are no angels, but they use the halo effect more often than any other tactic. The halo effect is the tendency for an individual to have a positive impression of a person, company, brand, product or service. For companies in retail, hospitality, and travel, it’s the kind of sentiment you want customers and employees to feel about your organization. But it’s often that trust that is exploited most frequently by hackers. The chart below shows the relative occurrence of how often hackers use the halo effect, as well as other cognitive biases in their spam and phishing schemes.
Relative Usage of Cognitive Biases by Hackers
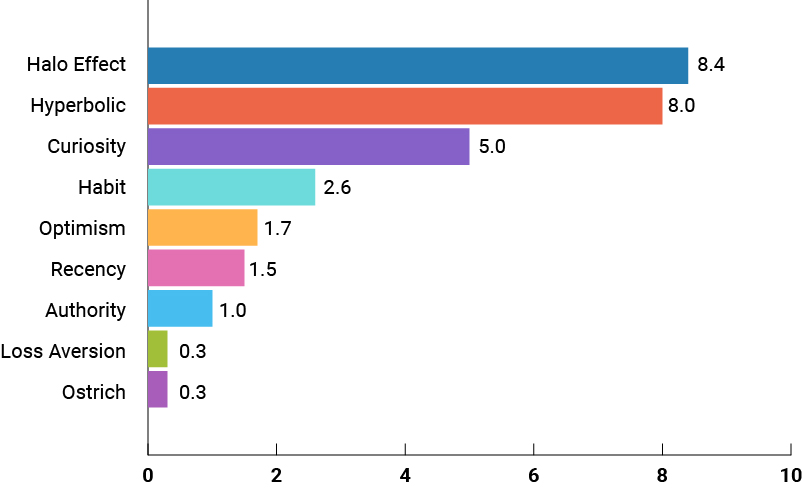
In addition to taking advantage of trusted brands, hackers are also targeting employees’ preference for receiving a small reward sooner rather than a large reward later. Hyperbolic discounting, in which an employee is immediately rewarded, coupled with their curiosity for receiving exclusive and secrete offers designed just for them, are the second and third most popular cognitive biases that hackers exploit. Again, this is based on the foundation of a brand being trusted, reputable, and reliable; and for many employees, brand loyalty – once seen as a strength by the organization they work – can now be seen as a vulnerability by hackers.
Security Awareness Suggestions for Engaging Employees
In order to identify which employees at your organization are being targeted by hackers, you’ll first need to analyze your email security logs. Typically, executives or employees with specific roles such as finance, or those with external-facing roles are more often targeted than regular employees.
Interestingly, more tenured employees tend to receive more spam; likely due to the longevity of their email ID, which is increasingly accessible to malicious elements. The chart below shows a few examples of role-based or department-specific threats:
Department specific flagged email examples

Once you have these user groups identified, you’ll need to analyze what themes are most prevalent in the emails they received, and what specific actions hackers are asking them to take. The chart below on the left shows that there is a small fraction of highly targeted users while most employees get at least some spam. In conjunction with the chart on the right, the majority of those targeted spam attempts contain a malicious URL.
Vulnerable Users Targeted by Spam
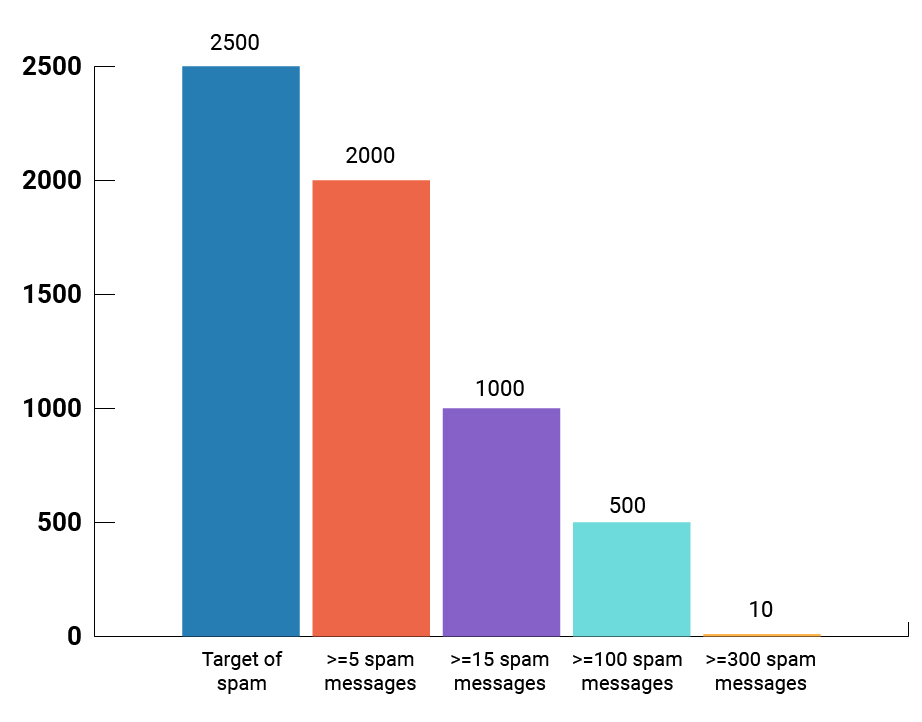
Spam Messages Divided by Type

With an understanding of how hackers are targeting which employees, you can design security awareness trainings that coach users not to engage with, but report spam instead. You can also implement security controls that safeguard their email addresses, which can lead to a reduction in the number of employees targeted.
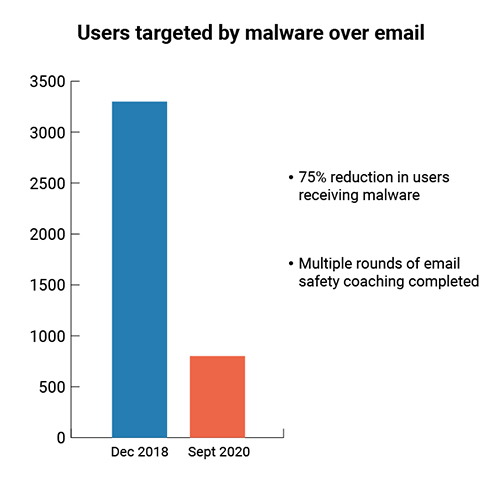
O365 Malware - 75% reduction in users receiving malware
The combination of security controls + security awareness training can lead to a measurable reduction in the number of phishing emails received and mistakenly acted upon. For example, the chart above shows the right security controls can lead to a 75% decrease in the number of users who received malware over a time period of less than two years. Coupled with a tailored program that has multiple round of email safety coaching and training, organizations can equip employees with the knowledge they need to identify the cognitive biases hackers are trying to manipulate, and take the correct action in reporting any phishing and spam messages they receive.