“It does not do to leave a live dragon out of your calculations, if you live near one.” – J.R.R. Tolkien
In 2022, ransomware is the live dragon for many companies working to develop incident response plans. According to Fortinet’s Global Threat Landscape Report, the first half of 2021 saw a 10.7x increase in the number of sensors detecting ransomware variants compared to the previous year. Throughout the latter half of 2021, ransomware remained at that elevated level with approximately 150,000 individual detections per week.
High-profile attacks have further demonstrated the financial and reputational impact a ransomware attack can have as “Kaseya” and “Colonial Pipeline” become names synonymous with ransomware. As a result, organizations now living with the reality of a potential ransomware attack are prioritizing plans for prevention and incident response plans in the event their defenses fail. But what goes into an incident response plan? Who should be involved, and how often should you test it?
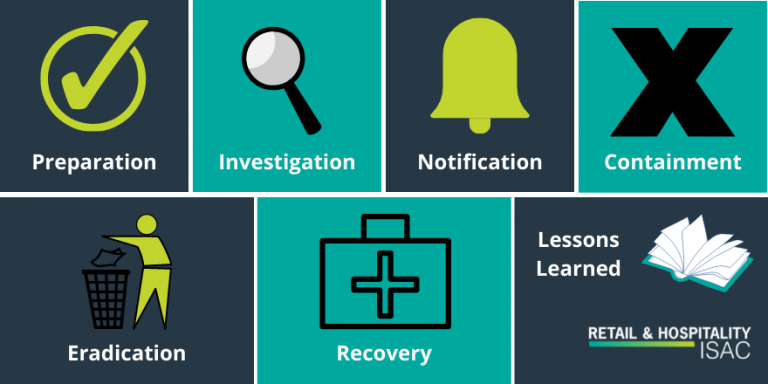
Here’s a guide for the most important factors to address in your ransomware recovery incident response plan:
Preparation
Your ransomware incident response plan should be written with input from all of the relevant stakeholders, including your cyber and IT teams and also your leadership, legal, financial, and communications teams. Gathering these groups together for a tabletop exercise to run through a what-if scenario and determine what actions need to be taken by each department, will help determine what needs to be documented in your plan. When sitting down to craft your incident response plan, the group should evaluate your data assets and determine the potential cost of a ransomware attack, taking into account factors such as losses from downtime and brand reputation. This will help you prioritize what data should be highly protected when configuring policies such as least privilege and setting up segmented networks.
In addition, establish recovery objectives to help evaluate the effectiveness of the response and keep response focused on goals that are most important to your business. These conversations will help your leadership team understand the importance of the incident response plan and how it feeds into their overall business continuity strategy.
Your ransomware incident response plan should act as a guide for what to do in the event of a suspected attack. Having this guide in place will help you act rationally and avoid needing to scramble to get things in motion. Train employees on their role in the event of a breach. Locate vendors and get approval for the projected cost of outside services if you don’t have the staff in-house to carry out all pieces of your plan. The better prepared you are before the attack, the more efficiently you will be able to respond, stop the spread of an attack, and limit downtime for your network.
Also outlined in the incident response plan, it is critical to maintain good Operational Security (OPSEC) and have out-of-band communication channels established, such as non-work phones or webmail accounts. A common tactic by threat actors is to compromise enterprise email accounts and look for emails containing “hacker” or “investigation.” If investigation details are known to a threat actor, they can pivot to another part of your infrastructure and re-tool, making it exceedingly difficult to detect them again. If you suspect a threat actor has gained access to enterprise communications, you should activate your out-of-band communication channels.
Detection and Investigation
As part of your plan, document your threat alert systems and procedure for confirming a potential ransomware incident. Once the attack is confirmed, the next step is understanding the extent of the attack. How did the attack occur? What type of ransomware is used? How far has the attack spread? Has your data simply been encrypted, or has it also been exported for potential use in a double extortion attack? You will need to perform a forensic investigation and collect evidence, including system logs, disk images, etc. If you do not have the capabilities in-house, part of your incident response plan should be locating a vendor who can perform these services.
Notification
Your incident response plan should have a list of contacts documented that are to receive a notification or an invite to a status update meeting. Teams representing legal, communications, and IT are essential to notify, along with leadership. Your plan should outline the conditions, like the severity or type of incident, that guide who is to be notified, by whom, when, and how much information will be released to them.
If personal information has been stolen, you may be required to disclose this information to consumers under laws like GDPR. What is your policy for notification of other stakeholders, such as your Board of Directors?
You’ll also need to report the attack to law enforcement. As part of your plan, do some research on the information needed to report to various entities, such as CISA or the Internet Crime Complaint Center, so you make sure that you collect all of it during your forensic analysis. If you’re in the U.S., develop a relationship with your local FBI field office now and build their response into your IR plan.
Containment
Once ransomware is confirmed, you need to attempt to contain the attack by locating the initial entry point. Is the infection confined to one machine that can be taken offline? Has it spread to a portion of your network or the entirety of your systems? While writing your plan, take into consideration the current segmentation of your network and the business impact of taking systems offline. You may be able to make improvements while writing your plan that can reduce your vulnerability in the event of an attack.
Eradication
Before you restore your data, you must ensure the ransomware and threat actor have been removed from your systems and network completely. This includes fixing the vulnerability that may have allowed initial access as well as locating any additional back door access that the attackers may have planted, including accounts they may have created, like for your VPN.
Ransomware Resilience Planning Guide
Recovery
This is a great time to evaluate your current backup systems. Do you have continuous backup, which updates every time a change is made, or near-continuous backup, which backs up in intervals? Are your backups immutable and stored offline, separate from your network? While restoring your data, you have the option of a complete restore from before the ransomware infection began, or restoring specific files based on when they were infected, which may reduce data loss in the event the attack was in the system for an extended period of time, gradually corrupting files. Your response plan should address potential data loss and how to reconfigure your systems to get back online.
Lessons Learned
In your IR plan, you should lay out your post-attack plans, which should include an incident report, a hotwash of what went wrong, and measures to improve security to learn from the attack. If you already had an incident response plan before the breach, review it to see how it can be updated, what worked, and what failed.
Too often, organizations will create an incident response plan and then never look at it again until it is needed, by which time it is too late. After creating the incident response plan, you need to test it regularly to make sure what you’ve laid out in theory will work in practice. You will never be able to plan for every exact scenario that may occur. You won’t know what type of ransomware you’ll be hit with or whether the source will be a phishing email or brute-forced credentials. That’s okay. The point of the plan is to have a reference and a guide for what actions should be taken. It is not meant to be a comprehensive what-if with every possible variable.
Members have additional access to ransomware resources such as malware trend reports and daily intelligence briefings, as well as peer-to-peer sharing opportunities such as the Incident Response Working Group. Learn more about RH-ISAC membership.