As we approach this 2022 holiday season, retailers will be faced with myriad pressures, some a continuation of market conditions from years past, others a bit more unexpected. Supply chain challenges remain, but instead of empty shelves, there’s a twist — driven by changing consumer preferences and buying behaviors. Red-hot categories like apparel and home goods cooled, forcing major retailers to revise their Q4 earnings and their promotional strategies to clear out excess inventory. Other pressures like inflation, low consumer confidence, and fears of a looming recession raise the financial stakes for retailers who must continue to compete for a slice of the consumer’s stricter holiday budget.
Although it’s clear that competition among retailers will be fierce, bad actors will also prove to be formidable retail opponents as they adjust their tactics and techniques to capitalize on market pressures and industry trends for their own financial gain. Based on Akamai’s observations, we expect increased activity in both bad bots and good bots — as well as in application and API assaults — in what’s already been a turbulent run up to the holiday season.
Bot trends reflect a shifting retail landscape
Setting the stage for 2022 requires that we take a quick look back at last year’s data. Starting in October 2021, Akamai witnessed the onset of a surge in malicious bot activity that lasted through early January 2022. This made sense at the time as retailers battled compounding supply chain issues and product shortages that attracted grinch bot operators intent on scooping up limited inventory ahead of actual customers to resell at higher prices in secondary markets. In the United States, in particular, consumers were encouraged to begin their holiday shopping early, and when they showed up, the bots did too. The rise in bot activity also corresponds to the 226% increase in credential stuffing attacks during this same holiday stretch as bad actors tested username/password combo lists in hopes of successfully accessing an account. But then, in March 2022, we see bot volume trends start to shift in an interesting — and unusual — direction.
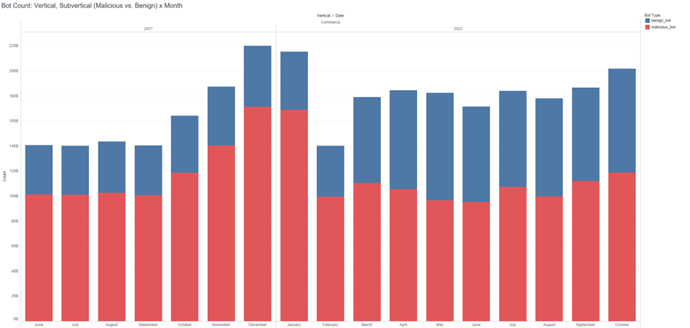
Although overall activity remained elevated, the mix of “benign vs. malicious” bots began to morph, with Akamai observing an approximately 103% increase in good bot traffic over the last nine months (Figure 1). The percentage increase in benign bots starting in March 2022 mirrors changes that reflect both broader and retail sector-specific trends – and headwinds.
It’s pretty straightforward — bots are great for automating repetitive and mundane tasks as well as more complex business activities. And as companies transition to digital businesses, they move toward robotic process automation as a way to help this transformation. For example, these bots could be your IT department pinging the website frequently to make sure it’s performing as expected, or you might have added some partners who use bots to check inventory by pinging your product catalog.
If we zoom in on retail industry pressures, the increase in good bots corresponds to post-peak pandemic woes and demand miscalculations. For many retailers, products intended for the 2021 holiday season arrived late due to supply chain slowdowns, leaving many companies with a glut of inventory in warehouses or the need to liquidate goods. Many also experienced a mismatch of supply and demand — especially within the home and apparel categories — which additionally contributed to product stockpiles. Months earlier, retailers couldn’t keep items on shelves. Fast forward to early 2022, and the script was starting to flip, as illustrated by bot activity.
The shifting landscape brings discounted prices
With excess stock, the market incentive for bot operators to hoard and mark-up holiday items (when demand exceeded supply) was eliminated as this type of abusive behavior became less profitable. Instead, we believe the rise of good bot volume — think coupon searching bots, comparison searching bots, and others — is a result of retailers having to offload goods at heavily discounted prices.
This makes sense as these types of bots would be operating in overdrive to monitor and scan for the latest pricing and availability information. Although these bots may not be considered malicious per se, some good bots can lead to unwanted activity that impacts the customer experience and the retailer’s conversions. A flood of coupon bots and comparison shopping bots could cause pain in two ways. First, by potentially slowing performance as they continuously ping and monitor your site for real-time pricing information; Second, by then using that information to lure customers away to a competitor or entice them with a coupon to which they aren’t actually entitled, which could lower profits.
Motivations are also shifting
Aside from noisy good or known bots, there are still bad bots whose operators may have different motivations this year. As noted earlier, inventory hoarding may not be as profitable as it was last year as the retail tides have turned. Instead, scraper bots may account for a bigger slice of overall volume.
For years, malicious actors have been using these types of bots to scrape content from a retailer’s site and applications, stealing product specifications, pricing, availability information, and other data. This content can then be used to create fake sites intended to phish or scam your customers. Unsuspecting consumers who visit the imposter sites could lose their credit card information and other assets, while you lose their brand trust and loyalty. And content scraping isn’t just for malicious phishing sites. Your competitors could also be using scraper bots to ensure they’re always just a tiny bit cheaper than your prices for the same items. The end result is the same — the retailer stands to lose out on customer loyalty as well as the bottom line.
Travel/hospitality subvertical caught in the bad actor crosshairs
By diving deeper into our commerce data, Akamai also observed interesting bot trends against our global travel and hospitality subvertical. Starting in the summer of 2021, malicious bot activity steadily began to increase and peaked in October 2021. The rise in bot traffic aligned with consumers trying to book hotel and airline reservations ahead of November and December holiday travel. Then, moving into 2022, bot traffic began to steadily increase up 54% YTD (Figure 2). This 10-month consistent rise in overall bot volume was most likely driven by known (good) bots, like travel aggregator sites, doing price and inventory scraping as consumers began opening their wallets to make post-pandemic vacation and travel plans.
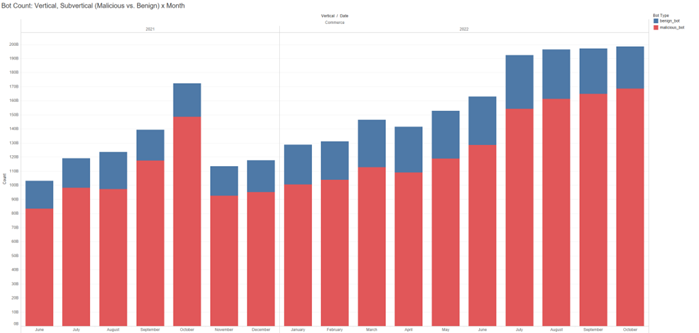
On the malicious front, the timing also signals that bot operators were busy targeting the loyalty and reward points that many customers had accumulated — but not cashed out — during the height of the pandemic. This type of activity typically presents itself via credential stuffing bot attacks that can lead to account takeover (ATO). A general increase in bot activity can also cause financial pain for travel and hospitality organizations. For example, every bot that hits a site from a price aggregator or third party can generate a paid query to a reservation system, increasing operating costs.
The rise of local file inclusion
If malicious bot attacks weren’t enough, the travel and hospitality vertical also felt the brunt of application and API assaults against web-facing assets. As part of a larger commerce trend starting in December 2021, Akamai data reflects an approximately 222% surge in local file inclusion (LFI) attack volume from the month prior, significantly outpacing cross-site scripting (XSS), which had been the predominant attack vector (Figure 3). These sustained levels of LFI attack activity have carried forward throughout 2022. When we compare Q3 2022 to Q3 2021, LFI attack activity growth increased by approximately 324%.
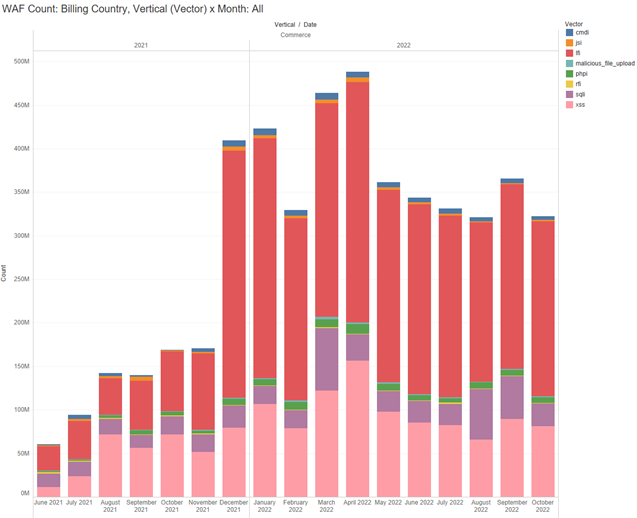
The rise in LFI may reflect the attacker’s desire to move away from just data exfiltration via SQLi — once accounting for approximately 79% of web application firewall (WAF) attacks against commerce — and instead use LFI to abuse vulnerabilities in web applications to expose sensitive files on a web server. LFI can also be used for attack chaining, leading to XSS or remote code execution (RCE). Perhaps attackers are taking advantage of the COVID-19–induced rush to deploy new applications and technologies by searching for LFI vulnerabilities and other security gaps to exploit. Another contributing factor could be the proliferation of containerized environments that may be running older images that are more susceptible to older attacks — like buffer overflow — thereby increasing LFI scanning requests.
How to keep bad actors and bad bots at bay this holiday season
Get more refined in your good bot strategy. Define which good bots you want to allow and which you want to slow down or block. For example, you might want to allow bots from the top three coupon vendors to come through but to block all the others. Or maybe you want to only allow partner bots during off-hours but to restrict them during peak times for human consumers. At the end of the day, not all bots are equally valuable to your business, so consider slowing down or blocking the less attractive ones while allowing the revenue-enhancing ones to pass through unhindered.
Be alert to evidence of an attacker moving through the ATO kill chain. Credential stuffing remains the No. 1 bot use case for attacks against retailers, and there are some recognizable signs that bot operators have you in their sights. Threat actors often start preparing for full-scale credential stuffing attacks with testing against the target environment. If you observe a small spike in failed logins leading up to key holidays like Black Friday and Cyber Monday, it could be a precursor to a larger assault. As with other types of malicious behavior, discovering and stopping bot attackers early in the weaponization and delivery phases of the ATO kill chain is a better defense against online fraud and account abuse.
Continue to keep WAF rules updated and in deny mode to defend against zero-day exploits, malware, and more. For many organizations, the WAF serves as the first line of defense to keep web applications protected and performing in an optimal manner. When the Log4j vulnerability was initially disclosed in December 2021, Akamai observed that approximately 58% of all exploitation attempts were made against the commerce vertical. Attackers seemed eager to take advantage of the seasonal frenzy when enterprise defenders and security resources were already stretched thin. As many organizations were left scrambling to identify vulnerable systems, malicious Log4j attempts made via web application traffic were stopped through updated Akamai WAF rules to help customers buy critical time to patch affected infrastructure or remediate infected assets.



