In North America and Europe, Black Friday and Cyber Monday have become an annual tradition for retailers — and consumers — to kick off the holiday shopping season. As a result of promotions and seasonal specials, items for sale during Cyber Week may be in limited supply and attract the attention of bot operators looking to score sought-after goods. These scalpers love a good deal because it opens up opportunities for them to make a profit on the resale market. So, the burning questions are: What are scalpers after this holiday season, and do all online retailers see the same influx of bot activity during these major sales events?
Because Akamai accelerates and secures the websites of leading brands and retailers globally, we have a front-row seat to all of the bot action that takes place during Cyber Week. From our vantage point this year, one thing became clear: The retailers most targeted by scalper bots were those selling electronics (TVs, laptops, etc), sneakers, and certain luxury items, which are easiest to resell on digital marketplaces at high profit.
Botnets designed for scalping and inventory hoarding generate large amounts of activity due to scraping for pricing, discounts, product details, and inventory information. But they may also be active and put pressure on critical workflows when logging in, adding products to shopping carts, and completing the checkout workflow. This often affects the legitimate users’ experience and prevents them from accessing the goods; the bot has the unfair advantage of speed and can complete the purchasing process ahead of real human users.
Select retailers and brands saw significant bot activity, while most saw little impact
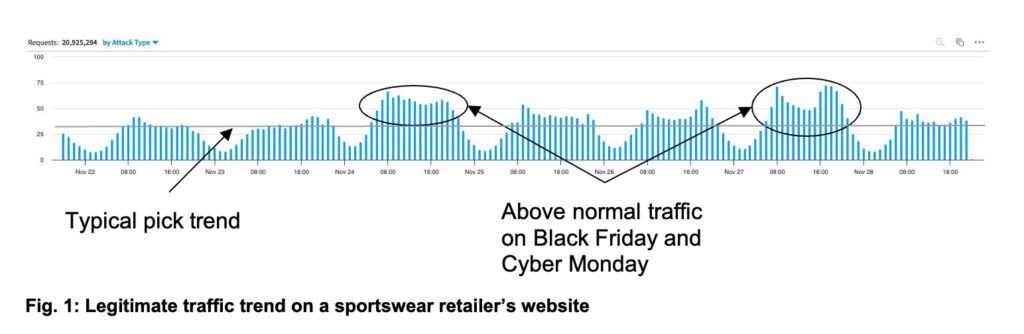
Overall, the increase in legitimate human traffic — naturally driven by holiday promotions — was significant for most commerce websites, while bot activity remained more or less the same. For example, the human traffic trend surged during Cyber Week for a major sportswear retailer focused on the US market, with above-average traffic during Black Friday and Cyber Monday shopping days (Figure 1).
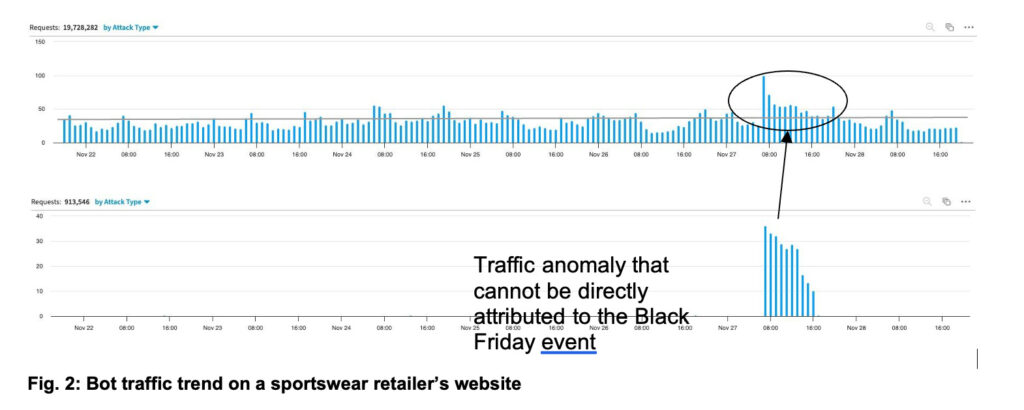
In contrast, the bot activity for the same period remained largely flat, except for a traffic anomaly that, after verifying the URLs requested, could not be directly attributed to a Cyber Monday sales event (Figure 2).
Did any retailers see excessive bot activity? Yes, high-end fashion retailers
In contrast to commerce sites that saw little increase in bot traffic, a retailer selling a sought-after luxury item saw increased bot activity that started on Thanksgiving Day and lasted beyond Cyber Monday. For our analysis, we only considered bot traffic that began during the period of interest; this bot activity had never been seen before against this customer.
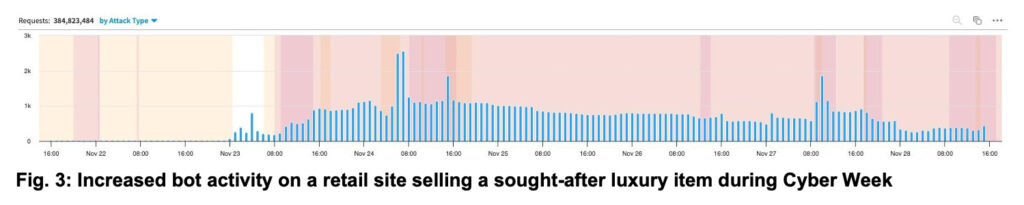
Botnet activity started in the early hours of Thanksgiving Day, continued to increase on Black Friday, then slowed down over the weekend — only to return with renewed strength in the early hours of Cyber Monday (Figure 3). Based on our data, we can attribute this activity to seven different botnets.
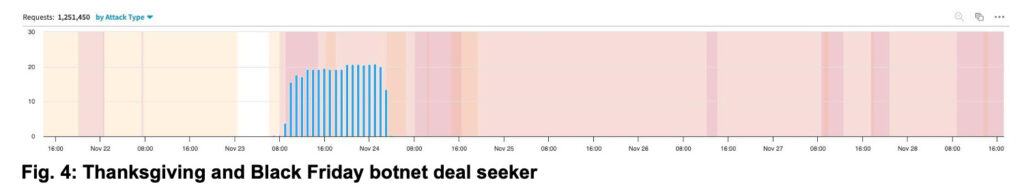
Some of the observed botnets were active throughout Cyber Week, while others were only active for a short period. This is the case for the first botnet shown in Figure 4, which was active only for the Thanksgiving and Black Friday shopping days. To understand the true intent of this botnet, one must look at the URL requested. In this case, the botnet only seemed to be interested in checking the inventory of 62 specific items in various sizes.
Additionally, one can also determine the operator’s motivation and experience by looking at the sophistication of the botnet. Two important aspects to analyze are the botnet’s scale and the request’s fingerprint quality; that is, whether it includes all the expected characteristics of a request coming from a real web browser. In this example, the botnet was sophisticated, with inbound requests from 11 different networks distributed across seven countries, including the United States, Brazil, and China. The fingerprint was also sophisticated, with requests over HTTP v2.0 that included the set of expected HTTP headers corresponding to the latest version of Chrome. Most requests came from residential IP addresses, making this botnet more challenging to detect.
Some observed botnets against this same customer, however, were only interested in capitalizing on Cyber Monday deals (Figure 5).
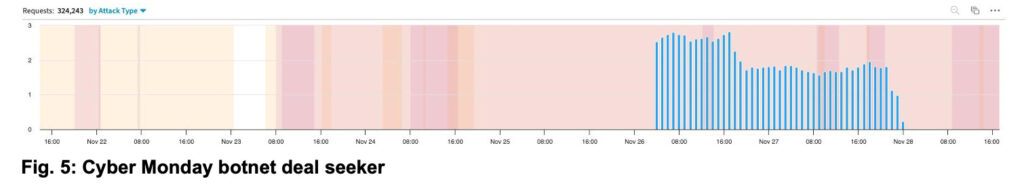
This particular botnet deal seeker was scraping the price and discount rate for tens of thousands of products across the site’s online catalog. In this instance, the level of sophistication of the botnet was much more basic, with requests from a single cloud provider and a simple HTTP v1.1 header set advertising a unique Chrome version that is more than a year old. Most websites and modern web browsers support and prefer HTTP v2 and v3, which help accelerate page load time. Requests over HTTP v1.1 and from a cloud provider are highly unexpected. Also, modern browsers auto-update and new versions see rapid adoption. This makes requests coming from old browser versions stand out. Both these characteristics are commonly associated with bot activity.
The botnet shown in Figure 6, however, was active for five days and continuously checked the inventory availability for 26 different models. Again, the data highlights a specific interest of the bot operator, indicating a scalping motivation.
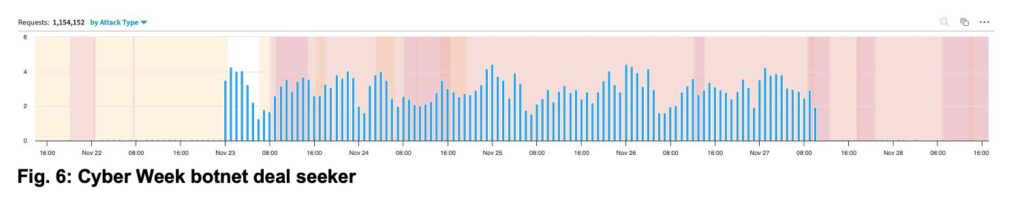
With respect to sophistication, the bot operator also fell short since requests came from 12 different outdated versions of Firefox (more than a year old). The requests were made using the more recent HTTP v2 protocol. However, several anomalies were found in the HTTP header set, mainly with the order of the header and some unexpected headers.
Was there any significant abnormal activity seen during login and account creation?
Scalpers are usually well-prepared. There was no significant increase in account opening abuse on the account registration endpoint. Scalpers often open fake accounts on the retail site ahead of time and use them to check out products during the sales event. As discussed in an Akamai blog post on account abuse, scalpers often create accounts using disposable email addresses on domains they own and manage. This gives them the freedom to create as many inboxes as they need. During Cyber Week, we saw evidence of fake accounts used to log in during the checkout workflow using email addresses on disposable domains such as duschgelmail.com registered on namecheap.com or sablx.com registered on squarespace.com. Both namecheap.com and squarespace.com offer low-cost domain registration so scalpers commonly use them.
Conclusion: Bot operators are becoming more selective in their scalping endeavors
Following the usual hype leading up to Cyber Week, we expected a lot more activity across our retail customer base as we continue to observe steady growth in bots that target digital commerce organizations. However, we discovered that scalper bots are opportunistic and they go after very specific products and brands to obtain limited availability items they can resell for a profit. A more narrow focus on select products may indicate that the secondary market for the majority of retail items is weaker this year due to economic conditions and inflation pressures. At the end of the day, everyone loves a good deal, bots included.



