For many enterprises, zero trust has emerged as the North Star of modern cybersecurity frameworks, designed to help organizations reduce their attack surface and risk by applying principles of least privilege or a “never trust, always verify” approach. Some zero trust-based security controls, like multi-factor authentication (MFA), are designed to add layers of login defense to prevent unauthorized users from accessing corporate networks, resources, applications, and systems. While MFA — especially solutions with FIDO2-level security — can be an effective way to reduce risk of an employee account takeover and stop malicious sign-in access to corporate assets, there are many other tools and techniques within the attacker arsenal of exploits to penetrate the perimeter, move laterally, then unleash malware across the network.
The retail attack surface is challenging to defend against malware
Because retailers face dynamic and complex attack surfaces — most both physical and digital — defenses must also stop lateral movement across networks as attackers seek to locate, exfiltrate, then encrypt (if ransomware) and block access to sensitive data. A successful attack could mean store operations and online commerce grind to a halt as critical systems and servers become inaccessible. It could also mean that credit card data, sensitive customer information, and company information like intellectual property is stolen, leaked, or auctioned on the dark web to the highest criminal bidder, causing further damage to brand reputation and the bottom line. Unfortunately, it’s not a matter of if but when an organization will be hit. With this in mind, it’s clear that rapid detection and remediation of malware propagation is critical to limiting the impact of an intrusion once threat actors are already past the front door in search of your digital crown jewels.
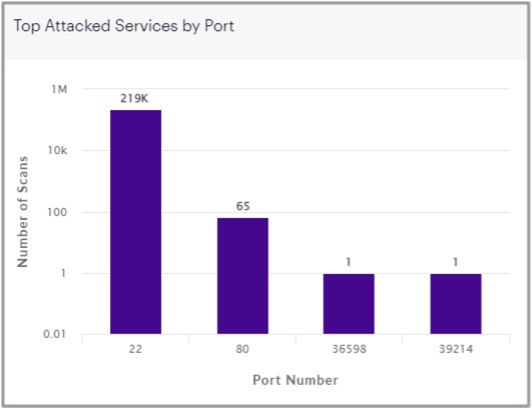
Driving complexity, retailers must contend with many potentially vulnerable endpoints into the network environment for malware to gain a foothold and spread. For example, in-store PoS terminals, IoT devices, tablets, and kiosks are commonly targeted by cybercriminals. And these are in addition to the most prevalent malware infection vectors like phishing emails, supply chain compromises (i.e., SolarWinds), exposed RDP ports, and attackers exploiting unpatched software and servers — a great example being the recent Log4j and Spring4Shell vulnerabilities. Our most recent data shows that Port 22, used for the SSH protocol (Secure Shell) communications and remote login access, was by far the most scanned and attacked port by malicious IPs.
Once inside, ransomware operators have even been known to scan for PoS software to locate and scrape credit card data for resale on the dark web in an attempt to make even more money alongside their extortion demands.
Geopolitical tensions raise the stakes — and introduce wiper malware
Adding pressure, escalating geopolitical tensions in the wake of the Russia-Ukraine war, and resulting sanctions have increased the risk of destructive malware attacks. These newly released wiper malware strains — like HermeticWiper, CaddyWiper, WhisperGate, and IsaacWiper — aim to damage targeted systems by erasing data, programs, hard drives, backups, and more. While some may include ransomware components, the adversary’s motivation is not focused on financial gain but instead is intended for pure destructive purposes of assets and infrastructure. That’s why both the Biden Administration and most recently The Five Eyes (FVEY) alliance released advisories urging organizations to harden defenses and improve security postures — now — in preparation for offensive cyber operations by Russia. Notorious ransomware operators, most notably Conti, have already openly stated they will act on behalf of the Russian government, threatening to attack Western infrastructure and leak exfiltrated data in retaliation for Ukrainian support.
But for years, retailers have been on the radar and targeted by some of the most active and prominent ransomware gangs — like REvil, LockBit, and AvosLocker — who have had a not-so-secret safe haven in Russia. In fact, a recent Microsoft study revealed consumer retail was the #1 most targeted vertical throughout 2021, ahead of the Financial Services sector, by organized ransomware operators and their affiliates. Another reported a 100% increase in ransomware attacks against the U.S. retail sector, based on publicly disclosed headline-making attacks. Expanding the target on a retailer’s back, hacktivist group Anonymous has threatened brands operating in Russia (many within the retail and hospitality space) unless they curtail operations and pull out of the country. Suddenly, many retail organizations operating internationally have found themselves caught up in the crossfire of geopolitical tensions with significant security and safety implications — both at home and abroad.
With cyberwarfare, there will be direct and indirect ramifications, collateral damage so to speak, regardless of whether an organization is specifically targeted. And as risk continues to increase and with sanctions driving the intended financial desperation of affected nation-states, it’s not shocking to assume that ransomware — and the resurgence of destructive malware not seen since the days of NotPetya — could hit the scene hard over the coming months and beyond. Capitalizing on the fog of war, the weekly average of cyberattacks against NATO corporate networks sourced from China was 116% higher than before the Russian invasion. In 2021 alone, the United States, United Kingdom, and Ukraine were the top three countries targeted by nation-states, with 58% of cyberattacks observed coming from Russia. For Ukraine in particular, adversaries were busy conducting espionage and intelligence gathering, laying the groundwork for future attacks as witnessed with wiper malware strains implanted within Ukrainian networks — prior to the physical conflict. A question to consider: What’s already within our own networks lying dormant, waiting for the right moment to strike?
Lessons learned from @Contileaks to aid blue team defenders
To gain access to an intended victim’s network, nation-state threat actors and ransomware operators alike primarily use RDP brute-forcing, stolen VPN credentials, and phishing to penetrate an organization’s perimeter defenses. Recently, the world was given a behind-the-scenes look at the operations and attack methodologies of Conti after one of their affiliates leaked internal documentation and source code in an act of retaliation after the group took a pro-Russian government stance. It’s been reported that Conti, one of the most profitable ransomware as a service (RaaS) crime syndicates, has earned upward of ~$180M in extortion payments across more than 1,000 victims, many located within the United States. Some researchers even estimate that Conti operators have made ~$2.7B in cryptocurrency over the past several years since arriving on the scene.
According to thousands of leaked internal documents and chat logs, it appears the ransomware gang and their affiliates employed common TTPs, such as scanning the internet searching for network vulnerabilities to exploit. Once the initial breach had been made, Conti operators then executed a “rinse and repeat” process of credential harvesting, privilege escalation, and continued propagation, using the same methodology over and over until they reached the domain controller (DC). Once the domain admin credentials for the DC had been obtained, the attackers then extracted most (if not all) of the other credentials — like password hashes — needed to access targeted assets, thereby achieving total network domination. Alongside their proprietary hacking and encryption tools, the criminal gang used “off-the-shelf” toolkits and programs like Cobalt Strike, Mimikatz and AnyDesk — common tools familiar to any pen tester or red teamer — to move undetected across the network for remote payload execution of the ransomware against high-value assets.
While the release of Conti’s internal documentation and communications gives organizations visibility into the attacker’s modus operandi and the ability to proactively address weaknesses, enterprise defenders require — and deserve — more. With a well-known cybersecurity talent shortage combined with increasing geopolitical risk, no organization will be able to hire their way out and bridge the gap — especially within the retail sector, where IT and security budgets are traditionally lower than other industries. Looking at Conti’s TTPs specifically and the number of victims that continue to be compromised via ransomware, it’s clear that threat actors who are highly capable and motivated will find a way inside, even with the best Zero Trust perimeter access controls in place. It’s important to recall that most of the gang’s time and energy was spent moving east-west across networks, undetected, until they had reached their intended destination. Therefore, a strategic shift and focus should be placed on stopping attackers in their tracks once they are beyond your first line of defense.
Taking a post-breach mindset to stop the enemy within
As both a Gartner- and Forrester-recommended cornerstone of implementing zero trust, microsegmentation can help detect and stop the lateral movement and propagation of malware across the network, providing the granular visibility that defenders and network teams alike require to fight back, limiting the blast zone of an infection. By applying Zero Trust principles of least privilege to critical workloads across the entire infrastructure, microsegmentation enables granular protection and deep visibility into east-west dataflows of applications and workloads via software-defined policies — to remove the adversary’s advantage. Retailers already have had to segment networks for years due to PCI compliance requirements, but many still have legacy implementations like physical firewalls and VLANs that drive operational overhead and complexity.
What’s worse, operational complexity leads to the inconsistent application of security policies and firewall misconfigurations that create defensive gaps — weaknesses that cybercriminals are eager to exploit. Microsegmentation also has been shown to improve SecOps productivity by 95%, lifting the burden from enterprise defenders and freeing up valuable incident response resources to focus on high-priority security events. Even if you haven’t fallen victim to a targeted ransomware attack, taking a post-breach mindset to stop the spread will help any organization move from a reactive to proactive security posture. At the end of the day, it’s all about defenses that work for you, and not against you, to better reduce the risk of a business-disrupting intrusion or breach, ultimately keeping your digital assets safe — and out of the hands of cybercriminals.



