This article is a repost from SecurityAdvisor

Security Challenge: Detecting Malware is Risky Business
Between May-August 2020, Emotet was the top malware variant reported in the RH-ISAC community, followed by Ursnif, Trickbot, and .jar malware files. Compared to other threats, intelligence shares concerning specific malware was not quite as common as business email compromise (BEC) attacks; however, even a small number of malware infections can have devastating impacts.
SecurityAdvisor recently conducted research across seven multi-national firms, which revealed that 20% of users typically account for more than 90% of malware infections. For a large organization with more than 10,000 employees, the 50 most risky users accounted for greater than 60% of malware detections, including the top 10 most risky users, which accounted for more than 20% of malware detections.
Traditional security awareness campaigns, however, often do not prioritize how risky behaviors are identified and associated, leaving the most vulnerable users unprotected and susceptible to repeating the same mistakes. Instead, programs tend to focus on metrics like phishing simulation click rates or training statistics that track engagement across the entire organization. While simulated phishing campaigns can target specific audiences, phishing is only one source of malware and simulated campaigns may not always reflect the real-world tactics of malware threats.

Thesis: Create Teachable Moments
Security awareness initiatives, therefore, need to integrate with cybersecurity priorities and focus on small number of high-risk users that account for the majority of the malware detections. One way to achieve this is to know what “teachable moments” will provide users with the insights they need, and at the right time. According to SecurityAdvisor, a teachable moment is when a user performs a specific activity that exposes the user and the organization to cyber risk. Through targeted engagement with high-risk users, organizations can identify when and how these teachable moments occur, and design security awareness initiatives that can address specific behaviors and significantly reduce the risk of malware infections.
Use Case: Leveraging Real-Time CrowdStrike Detection
To validate the thesis, SecurityAdvisor partnered with CrowdStrike, the leading endpoint detection and response (EDR) platform for malware, to run personalized security awareness campaigns. First, the CrowdStrike EDR platform identified the APIs that were collecting data by their endpoints, which was then leveraged by SecurityAdvisor to detect real-time “teachable moments” related to malware.
When a user engaged in risky behavior, it triggered a CrowdStrike detection and prompted SecurityAdvisor to deliver a targeted training session to the user, whether it was a poster, video, game, or module that reinforced best practices for avoiding malware infections.
The illustration below shows the most common teachable moments SecurityAdvisor has identified for CrowdStrike users.
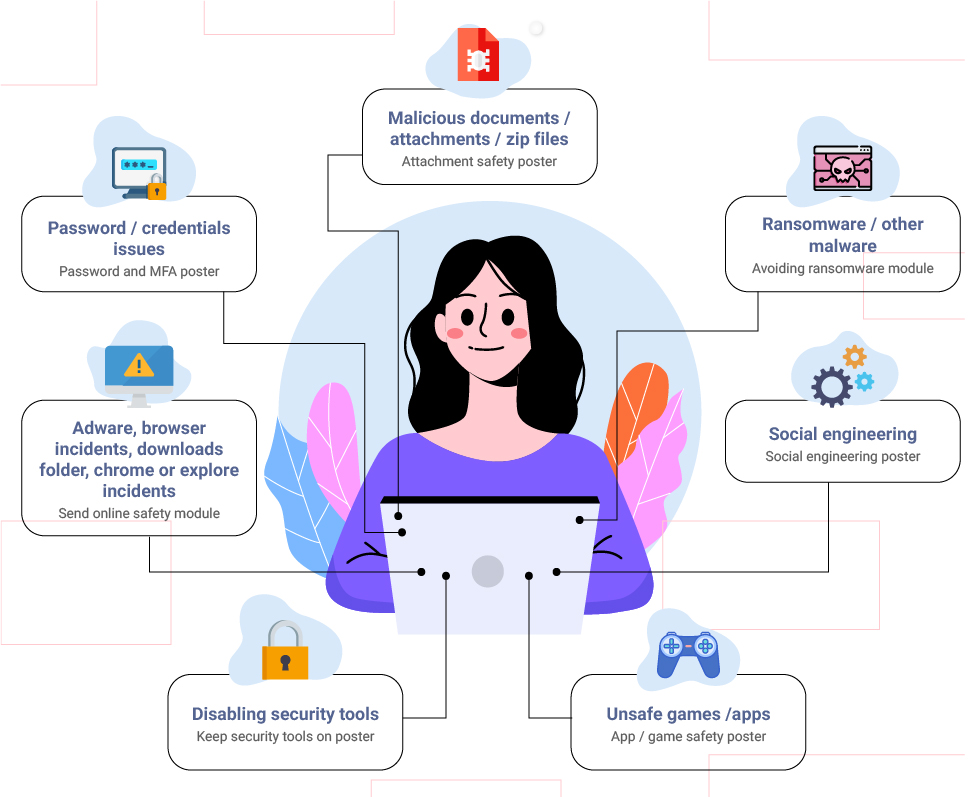
As SecurityAdvisor’s AI-driven platform examines the real-time data, they are able to identify the most prominent teachable moments for CrowdStrike users.
Results: Targeted Training Reduces Risk
Users were more than two times more likely to participate in personalized training sessions within two days of receiving an email, as compared to traditional security awareness campaigns. Teachable moments allow organizations to design training for specific employee behaviors, and as a result, SecurityAdvisor was able to deliver awareness lessons based on unique malware infection profiles and increase user engagement.
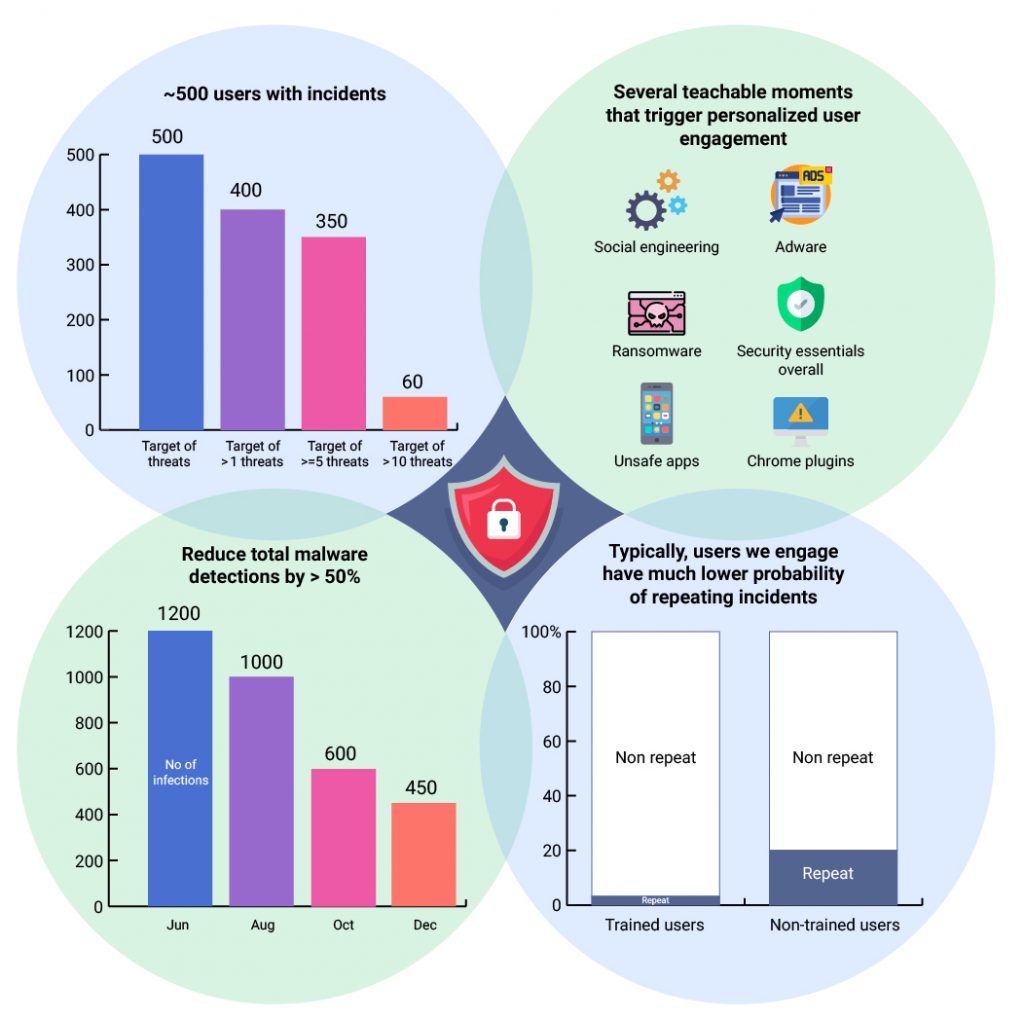
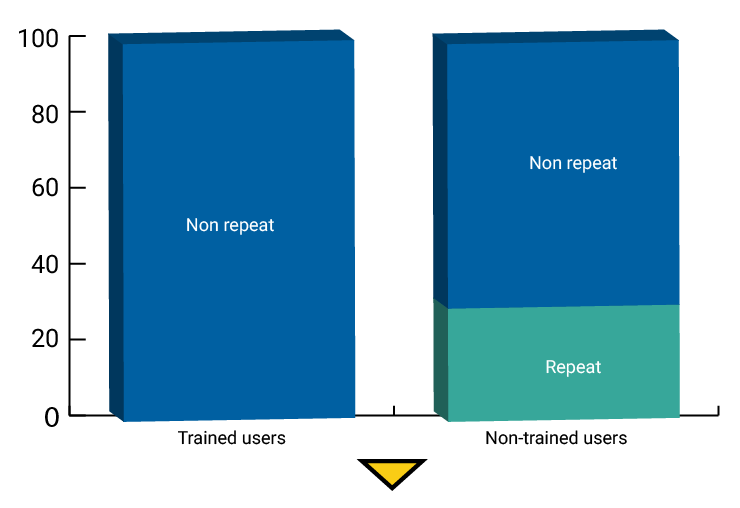
More importantly, over a three-month time period, there was a significant decrease in the number of malware incidents detected by CrowdStrike and other tools/proxies for email security and identity protection. The graphic below illustrates how risky employee behaviors were measured and reduced.
Measurable reduction in risky users
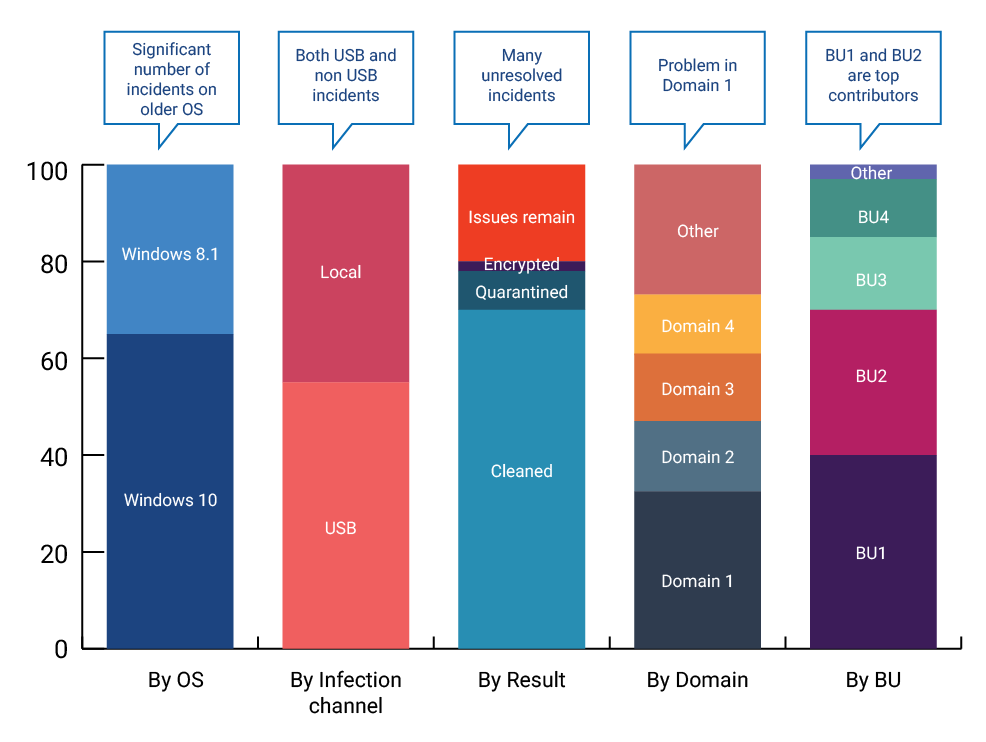
Identifying specific sources of malware, can allow organizations to drive even more targeted results. For example, SecurityAdvisor found that USB devices were a top source of infection for a customer with a large retail presence. The chart below illustrates that after a targeted three-month security awareness campaign for high-risk users with this profile, USB-related malware detections were significantly reduced or eliminated.
Key Takeaway: Collaborate with Your Cybersecurity Team
Reducing risk is no easy task, so security awareness programs should team up with their cybersecurity teams in order to understand the threat actors and their associated tactics, techniques, and procedures (TTPs). This will ensure that trainings replicate real-world threats in a timely and relevant manner.
Similarly, leverage their tools! Security awareness programs can enhance how cybersecurity detection tools like CrowdStrike are used and make an important shift toward measurable metrics that can be seen in real-time. These insights are invaluable for identifying risky employee behavior and designing educational materials and/or trainings that address these users.
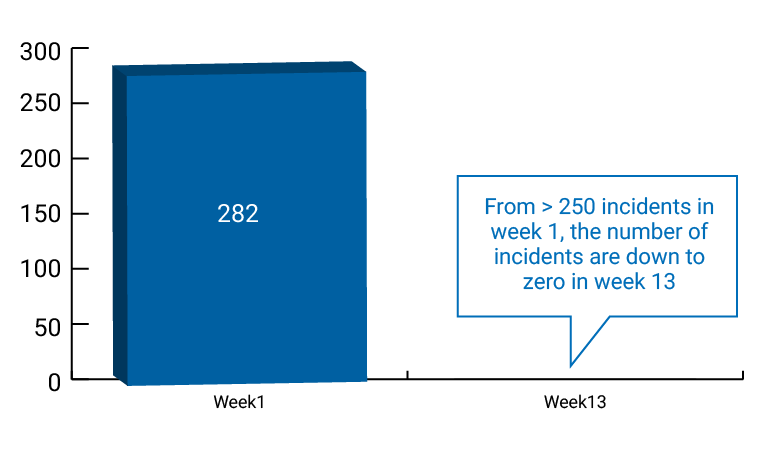
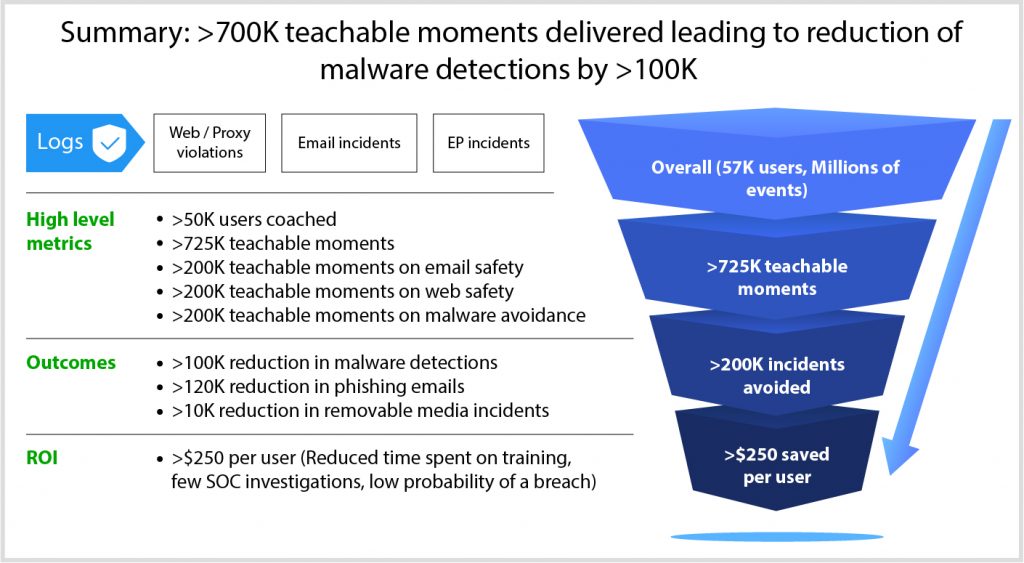
The illustration below shows how to measure RoI for a large set of 50000 users and focusing not just on training metrics but tangible security outcomes like reducing malware.
About SecurityAdvisor: an RH-ISAC Associate Member
SecurityAdvisor provides targeted security awareness lessons and trains users at the moment an incident occurs. SecurityAdvisor integrates with leading cybersecurity and detection platforms, like CrowdStrike, Palo Alto Networks, and more, to identify the users putting your organization more at risk and helps fortify these risky users to build an organization wide cyber immune culture.


