Last holiday season, the headlines were all about the excess supply and glut of inventory that retailers had to sell off quickly to capture revenue amidst tight competition and waning consumer sentiment. While this year has so far presented new macroeconomic pressures — which some argue might be getting worse — retailers have continued to build resilience within supply chains and evolve to differentiate themselves. And on top of these new challenges, retail organizations still continue to face ever-evolving attacks from threat actors intent on committing online fraud and abuse. From bad bots and account takeover (ATO) attacks to malicious scripts and audience hijacking tactics, retail organizations should remain vigilant as we press forward into this year’s traditional peak shopping season.
That’s why Akamai recently partnered with Foundry to investigate the effectiveness of specialized security defenses against the most prevalent online fraud and abuse tactics. Respondents were asked about four broad categories of fraud and abuse — bots, ATO, script protection, and audience hijacking — and how dedicated security controls improved business outcomes. While this research primarily focused on these areas from a security perspective, it’s also critical to recognize the reliability and performance implications, especially with the holiday season fast approaching. Let’s dive deeper into the actions retail organizations can take over the next 60 days to not only to better detect and mitigate malicious activity but also ensure a better performing and more reliable shopping experience.
But first and most importantly: 89% of survey respondents stated they had deployed a specialized third-party solution to help combat malicious bots. Of those organizations that had, 54% identified these specialized tools “significantly” improved their ability to identify and mitigate threats. And 47% also noted their improved ability to handle high-heat events and traffic surges — an important capability, especially during the holidays. If your organization hasn’t yet deployed a specialized solution for bot mitigation, it should be the number one action item on your list prior to peak season.
Be sure to invest in bot detection products or services that use advanced algorithms and machine learning to identify and mitigate malicious bot activity — things like behavioral analysis (monitoring user interactions to detect patterns that deviate from typical human behavior) and device fingerprinting (techniques to identify and track devices to detect anomalies that might indicate bot activity).
Now, let’s take a closer look at each of the four main categories of fraud and abuse that should be top of mind to prepare for this holiday season.
Malicious Bots: And Too Much of a Good Thing Can Also Be Bad
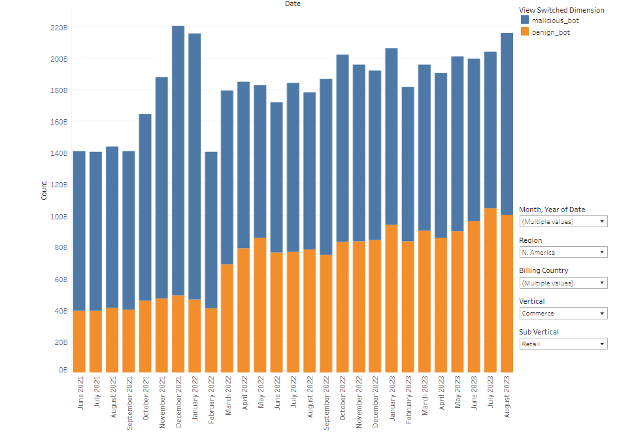
Bots can be designed for a variety of purposes, many of them malicious in nature. During the holiday season, these malicious activities can be used to overwhelm your application infrastructure in a variety of ways that could have a negative impact on your legitimate customers. Content abuse is one such method — where a bot or bot network scrapes your site to reuse content somewhere else. No matter the reason, delivering this traffic to bots costs you money and consumes resources that should be available for your real customers. To prevent content abuse, look to implement rate limits both sitewide and on critical endpoints that are resource intensive. Additionally, look to serve bot traffic cached, or pre-rendered, or even content delivered from a different origin that costs less and doesn’t compete with serving real customers. It’s important to reiterate that while good bots can be a great boost for business — think SEO or partner bots — this increased load can tip the scales to overwhelm your application and cause an outage — or, at minimum, the added load can slow down the site for the rest of your real users, not to mention extra costs. The need to manage both malicious and good bot traffic should be prioritized as both types continue to trend “up and toward the right” based on our commerce data from the past several years
Further protecting those critical API endpoints (think things like “Add to Cart,” “Checkout,” and “Update Shipping Address”), look to adjust detections to be more aggressive during the holiday season. However, increasing detections can lead to increased false positives (incorrectly identifying a real customer as a bot). So to offset this risk, look to deploy “challenges” — some sort of interaction with the user or their device (Google’s reCAPTCHA is a well-known one) — that allow real users to prove they are not a bot, while making it more difficult for bot operators to get through. You can even deploy a series of challenges, both active (the user must do something) and passive (the challenge is silently solved by the browser) to increase effectiveness and consume additional botnet resources.
ACTION ITEM: Implement Challenges and Rate Limiting. Integrate challenge(s) on forms and login pages to differentiate between human users and bots. Additionally, implement rate limiting to restrict the number of requests a user can make within a certain time frame, or, route requests to an alternate or cached origin. This helps prevent bots from overwhelming your systems and causing disruptions.
Account Takeover (ATO) Attacks: Adding Friction to the Fraudster’s Playbook
When a legitimate user’s account is compromised by an unauthorized source, whether it is manual or automated, it’s considered an account takeover (ATO) attack. Based on the Foundry survey data, 79% of respondent organizations had been targeted by an ATO attack within the past 12 months. Once in control of the account, the attacker can make illegitimate orders, steal loyalty and gift card balances, or resell the account to another attacker. Ideally detected before any actual impact can be inflicted, just the inconvenience of notifying or having to perform password resets for a mass amount of users can result in expensive and lasting damage to your brand.
Educating your users about security best practices can go a long way in preventing successful ATO attacks. Provide clear guidelines on creating strong passwords, avoiding password reuse across platforms, and recognizing phishing attempts. Regularly communicate with your user base through newsletters, in-app messages, or emails to keep them informed about the latest security threats and how to stay safe. Additionally, you can implement automated monitoring systems that can detect anomalies in user behavior, such as sudden location changes, unusual login times, or multiple failed login attempts.
The most effective way to secure against ATO is to enforce multi-factor authentication (MFA). MFA adds an extra layer of security by making it significantly harder for attackers to gain unauthorized access, even if they manage to obtain a user’s password. Require users to provide more than one piece of evidence to verify their identity. This could include something they know (password), something they have (a temporary code sent to their phone or email), or something they are (biometric data like a fingerprint or facial recognition).
ACTION ITEM: Implement Multi-Factor Authentication (MFA). Rather than simply trigger alerts or temporarily disable a user’s account when a suspected ATO attack is detected, instead enforce MFA as a step-up challenge to require proof the usage is legitimate. This allows real users to continue with their transaction but stops malicious activity from occurring without requiring intervention from the account owner.
Script Protection: Defending the Client-Side Attack Surface
Most often when we speak about “third-party scripts,” the concern is around performance impacts. It’s quite easy to add tags and trackers that help you better understand and monetize the behaviors of visitors to your site. However, each script can slow down the experience — in the worst cases, even to the point where conversions are negatively impacted. With the rise of web skimming and Magecart-style attacks, the concern with scripts has become more oriented toward securing the user experience and preventing data exfiltration. It’s therefore not surprising that browser script monitoring and management controls are now requirements of PCI DSS v4.0. Based on recent Akamai data, half of the JavaScript running on our commerce customers’ sites comes from third-party vendors, highlighting the increased risk to the client-side environment and potential for compromise.
Therefore, your site’s security is now as weak as the security of your weakest script provider. Attackers can inject malicious code into legitimate code libraries, giving them access to your customer data before you can even detect the exploit at your firewall. Good design practices like input validation and sanitization on form and other input fields are a great start. You can also ensure your Content Security Policy (CSP) is regularly maintained. CSP helps prevent web skimming attacks by limiting the execution of scripts to trusted sources only. It can also mitigate the impact of data breaches by preventing the exfiltration of sensitive data to unauthorized domains. But there are some downfalls to CSPs, as you can’t always trust that approved domains have not been compromised themselves. Additionally, maintaining an allowlist of trusted resources can be labor intensive and stunt developer innovation. It’s important to consider investing in tools that automatically and continuously track, inventory, and monitor the behavior of all scripts executing on your site for malicious activity.
But the most impactful thing your organization can do to protect yourselves and your customers from malicious scripts is performing regular software updates and patch management. Many vulnerabilities that malicious scripts exploit are discovered and fixed through updates. Regularly monitoring security advisories for the software you use, and promptly applying patches, helps minimize the risk of exploitation.
ACTION ITEM: Perform Software Updates and Patch Management. Ensure all critical updates are applied across your site, including and scripts provided by third parties. As part of the update process, ensure you have a documented reason for each third-party script included and can validate the authenticity of the code from the provider.
Audience Hijacking Prevention: Are Your Customers Being Lured Away?
As consumers have become less loyal to brands and more savvy at finding and comparing products across retailers, they have unknowingly become more susceptible to a variety of audience hijacking tactics. Audience hijacking occurs when unauthorized advertisements or pop-ups divert site visitors away from an online store to competing and sometimes malicious websites. During Cyber Week 2022, Akamai observed a 25% increase in coupon and price comparison extensions attempting to impact customer site sessions. These unauthorized ads may redirect customers to competitors — but can also redirect them to impersonator sites with the sole function of stealing customer data. Regardless of the tactic, your brand can easily become associated with a deceptive alternative and result in customers blaming you for a breach of personal data you may not have even been aware of or able to stop directly. Recent research shows that audience hijacking is estimated to disrupt 15% — and sometimes more — of ecommerce site visits. In the same report, 54% of retailers stated that customers encountering fraudulent offers through audience hijacking tactics that damaged customer experience was a severe problem for their organization.
While coupon extensions or affiliate programs aren’t necessarily bad, do you have full context or control over how they impact user experience — or your bottom line? Depending on your brand’s needs, consider exploring specialized audience hijacking prevention technologies that allow for deeper analysis and monitoring of client-side browser sessions to determine how pop-ups and browser extensions are affecting your customers’ path to purchase. Having visibility into in-browser behaviors should be a priority this holiday season.
ACTION ITEM: Implement alerts to monitor for potential audience hijacking. If you already have a specialized audience hijacking prevention tool deployed, it will allow for deeper analysis of client-side sessions to determine how pop-ups and browser extensions are affecting your customers’ path to purchase. Be sure it is active and has alerts set for suspicious behavior. If you don’t have specialized tools, look to other datasets that may provide some insights — things like increased bounce rates in real user monitoring or clickstream data, increased coupon usage or reuse in marketing analytics tools, or suspicious referrer sites popping up in traffic analytics.
Balancing Security and Performance this Holiday Season
This holiday season, retailers will be challenged with both competitive pressures — as consumers tighten wallets — and the ability to defend against online fraudsters. Your brand can take simple actions to be one step ahead of the most common fraud and abuse scenarios impacting you and your customers. Deploying specialized tools to detect and mitigate bots has proven to be a valuable investment, as evidenced by the Foundry survey results. This empowers you to better handle high-heat events like flash sales and product launches, reduce content scraping, and ensure less friction in the checkout flow for real customers, while increasing friction for malicious bots.
Beyond security, don’t forget to think about the performance and reliability impacts of fraud and abuse. Detecting and preventing malicious activity can reduce the overall cost of hosting your infrastructure, speed up your web performance, and prevent your site from being vulnerable to outages when under load.
When retailers appropriately balance security, web performance, and site reliability, they are able to deliver a safe, reliable, and secure shopping experience for their customers and stand out against the competition.



