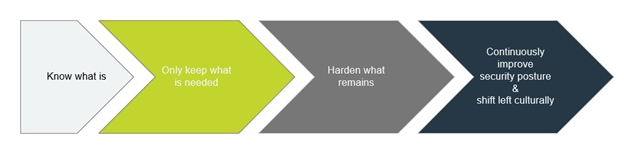
Based on the pillars discussed in the earlier series posts, nothing changes when approaching data security – we start with knowing what is – at a minimum, organizations need to identify and categorize sensitive, regulated, operationally critical data, etc.
Data Labeling and the Categorization of Critical Data Types
This process will involve mapping all the data repositories and their respective recovery sources. It is also essential to understand how the data is manipulated from a transactional process perspective, as some data is transient. In contrast, some is ordinal or incremental, which will significantly change forensic analysis and recovery strategies.
Basic Data Security-Related Controls Explained
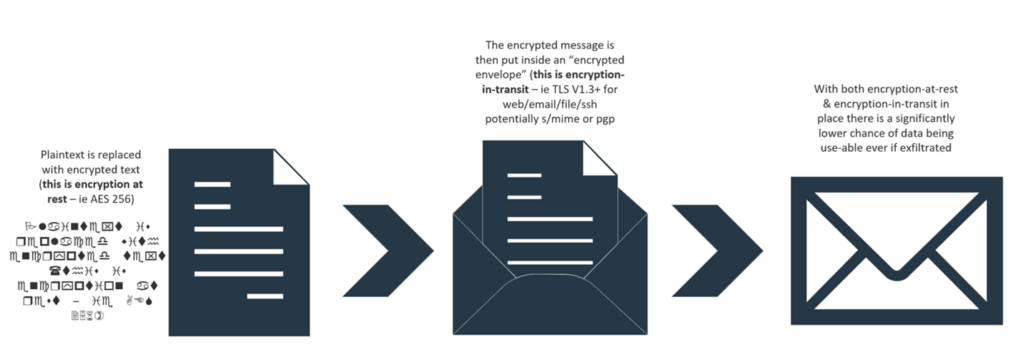
One of the simplest specific data security-related controls to disable is access to external data ports for inbound or outbound data transfer (i.e., USB, etc.). Although perhaps not the simplest to implement across an organization, encryption-at-rest and encryption-in-transit are the two most effective means of making data useless, even if exfiltrated. To explain the difference between the two, as well as each’s importance, check out the image below:
Data Loss and Prevention (DLP), User and Entity Behavior Analytics (UEBA) and Insider Threat
With critical data sets cataloged and the proper encryption in place, organizations should look at DLP policies and the associated tools to track critical data use in near real time. Additional logging and anomaly-related alerting should be put around access requests in context with defined RBAC profiles. If there is a defined Insider Threat team, these alerts should route to them and Incident Response (IR) for further investigation.
What the Future Holds in the Coming Quantum Computing Era
The last significant point related to data security – with the advent of quantum computing, data security becomes slightly more complex, if not immediately, definitely within the next decade. In market segments such as National Defense or the Defense Industrial Base this may already be a realized threat. As quantum computing technologies get further commercialized and more code-cracking capabilities become publicly available, new quantum-proof encryption will need to be implemented.
Have questions about zero trust? RH-ISAC’s Member Exchange is the home for discussions among retail and hospitality peers. Not a member? Learn how becoming a part of the RH-ISAC community could benefit you.
