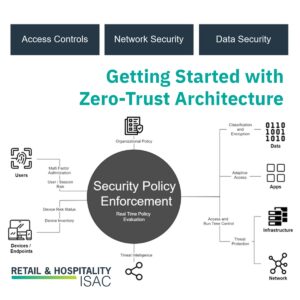
A Roadmap to Zero-Trust Maturity
Despite all the marketing hype related to ZTA, at the end of the day, it may not make sense for all organizations, particularly those in less risky environments to implement or pursue all components. That said, all organizations can learn from the tenets and leverage them to improve their security posture. In the preceding series,…
Read More