Now that we have it defined, how do we practically approach the path to zero-trust architecture (ZTA) and why does it matter?
Suppose we start the ZTA discussion by agreeing on a standard definition in its simplest form, i.e., limiting the impact of any unauthorized events by design. Many current industry definitions summarize the key points as assume breach, least-privilege- access, continuous authentication, being focused on data protection and real-time visibility. How do we get better at early detection, as well as limiting the inevitable impact in a metered and thoughtful way?
In November 2022, the Department of Defense (DoD) published a Zero Trust Strategy that lays out a systematic implementation approach for ZTA principles. Prior to that, CISA published Zero Trust Maturity Model as a pre-decisional draft in June 2021. In an effort to summarize these for RH-ISAC Members and to demystify ZTA, the suggested policy/process/tool changes are grouped into three categories: Access Controls, Network Security, and Data Security.

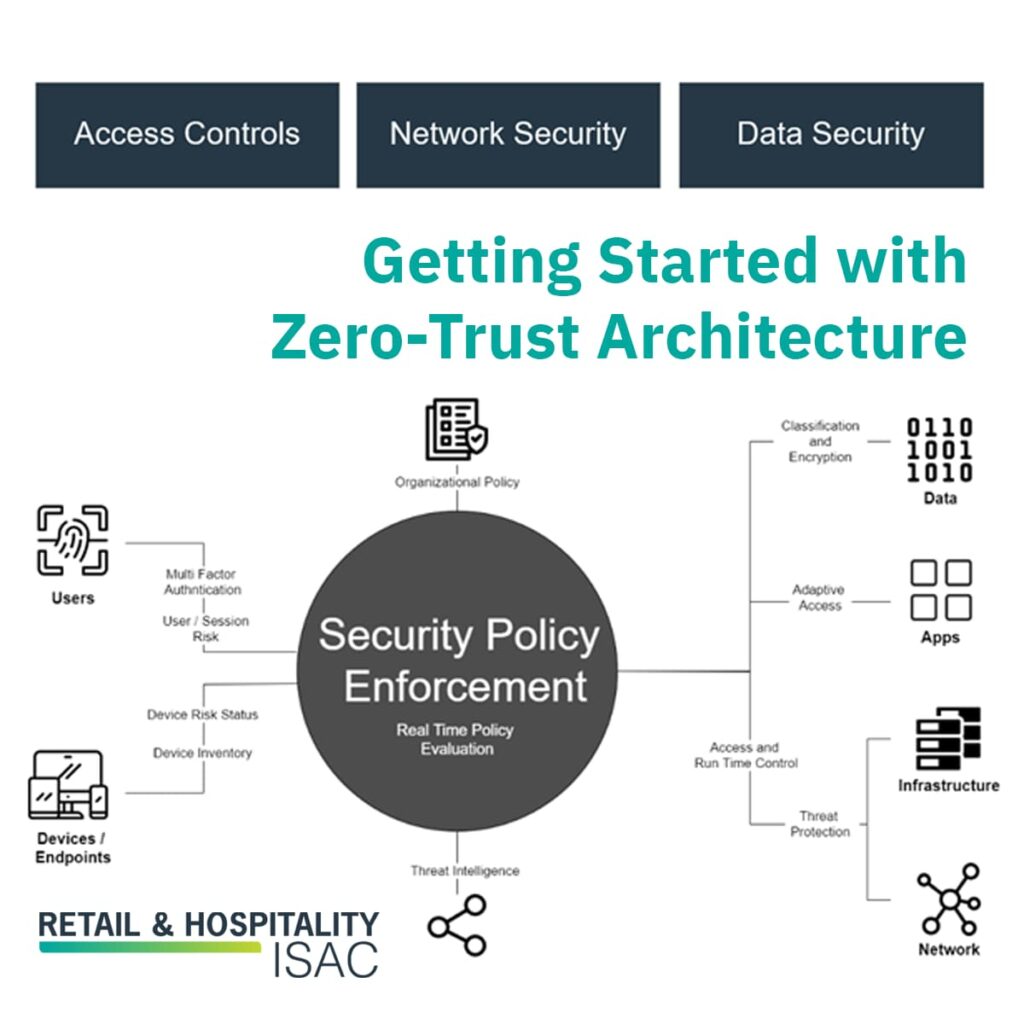
What does this ultimately look like in architecture terms? The image below does a good job of showing how many of the components get effectively integrated from a cyber fusion perspective:
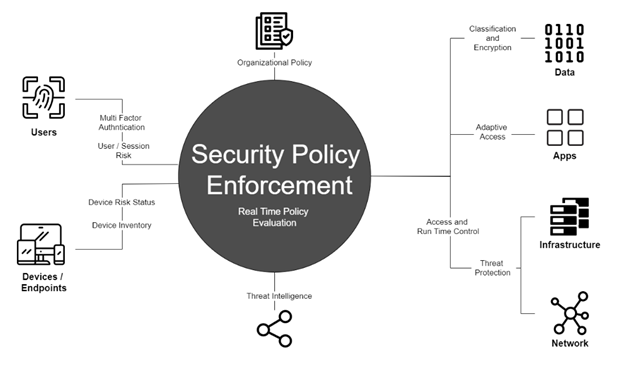
Image credit to: https://blog.miniorange.com/zero-trust-security-model/
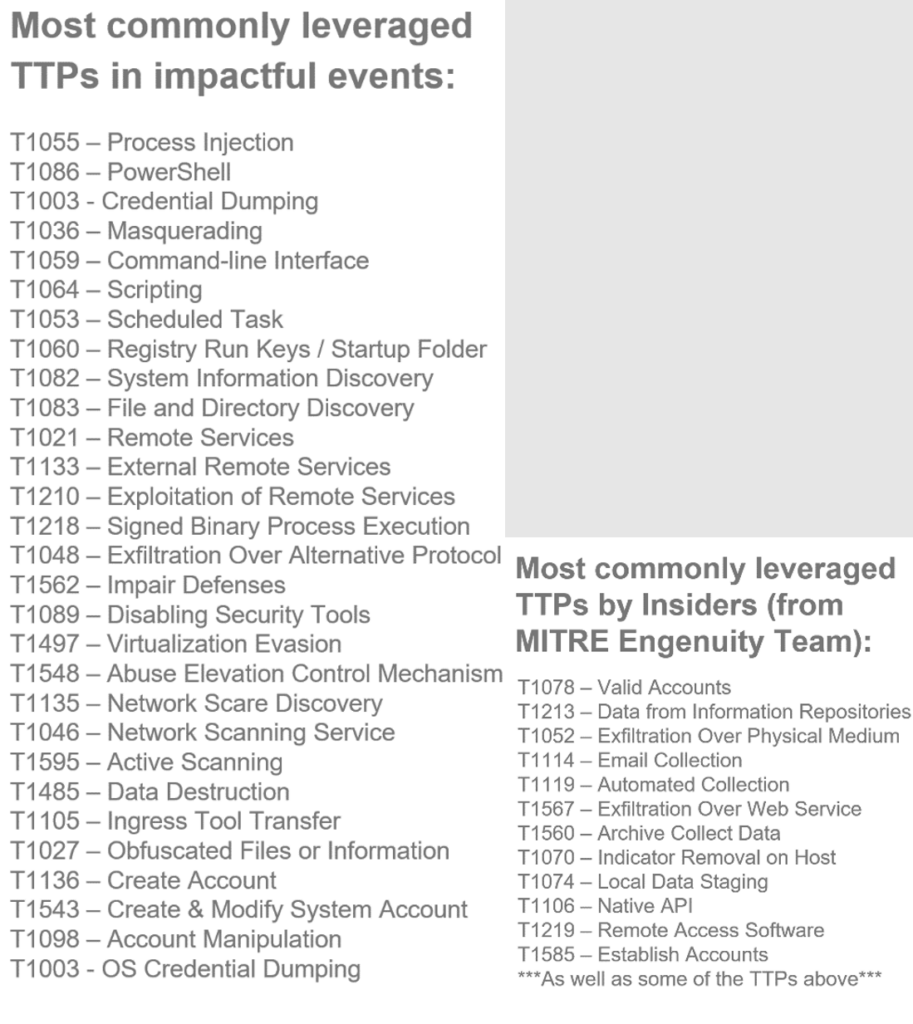
The recommendations outlined in the following series are focused on hardening one of these core tenets and were specifically targeted based on real-world MITRE ATT&CK-mapped incident data. Although there are currently 185 techniques and 367 sub-techniques, we can focus detection capabilities and hardening efforts around a specific list of 41 (11%).
Maturity Milestones
Before diving into the weeds, it is essential to start with a high-level understanding of the key milestones in terms of maturity:
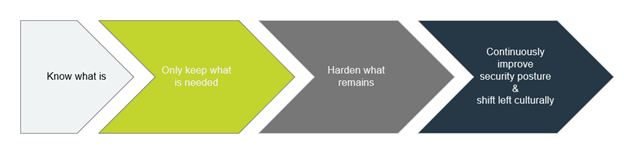
Know What Is: The quest to achieving ZTA starts with confirming an inventory (ideally dynamic) of active accounts, assets (both endpoints and network components), data sources, network communication protocols, business behavioral patterns, etc. The list continues but at a high level – we have to know what is.
Only Keep What Is Needed: Once the current reality is somewhat understood, often there are many low-hanging-fruit-style opportunities to improve security posture without impeding or altering any current business practices. Significant access-related process changes and network security improvements often mark this phase. The goal of the only keep what is needed phase is to confirm or define the organization’s actual attack surface by eliminating all vectors that are not currently leveraged for business operations.
Hardening What Remains: Beyond eliminating the basics, organizations eventually reach a maturity level where it becomes advantageous for the cybersecurity and security engineering teams to unite with their enterprise architecture peers to start hardening what remains. This phase will involve core systems being refactored to be anti-fragile from the onset.
Continuously Improve Security Posture and Shift Left Culturally: As the core systems become engineered for chaos, the lessons learned from these efforts will start to spread to the other development teams within the organization. Alerting and response will improve, and the partnership between DevOps teams and their security peers will shift from initially being an organizational expectation to a bi-directional survival dependency. If properly executed, this shift will yield a competitive advantage for years to come.
Have questions about zero trust? RH-ISAC’s Member Exchange is the home for discussions among retail and hospitality peers. Not a member? Learn how becoming a part of the RH-ISAC community could benefit you.