From the onset, access control is the most dynamic pillar in the ZTA implementation process. New accounts need to be created for legitimate business use, accounts likely need varying degrees of access, and account revocation for individual accounts and a mass list is always a concern.
Identity and Access Management (IAM) Basics
The quest towards ZTA supporting access controls starts with establishing identity and access management (IAM ) for the internal user population, often nesting core applications behind a SSO type functionality to track account activity across multiple applications. Additional security controls, such as phishing-resistant multi-factor authentication (MFA), should be implemented to harden these core accounts further.
These activities can be visually understood in the following graphic:
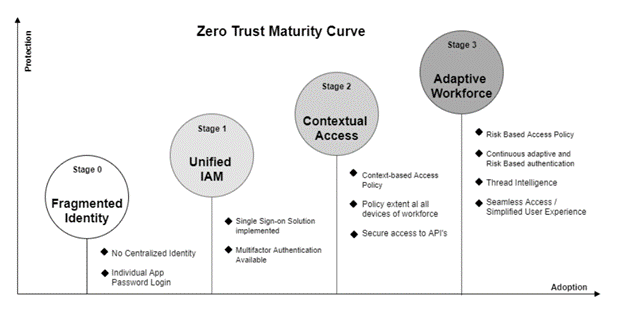
Image credit to: https://blog.miniorange.com/zero-trust-security-model/
In NIST’s 2019 release of SP-800-207, many of these primarily government-provided definitions were focused on the needs and concerns of the federal government. RH-ISAC members have many of these same challenges; however, for retail, hospitality, entertainment, or travel segments specifically — at the same time internal access controls are getting matured, there is also a shift from the legacy brick-and-mortar-only customer experience to various forms of physical/digital consumer-side interactions. With the desire to sell digitally comes the reality of digital-borne consumer fraud and new money-making schemes such as refund-fraud-as-a-service or FOPIS (From Online to Person In Store) fraud as discussed by Netacea in a presentation at the 2022 RH-ISAC Summit.
As the future of retail and hospitality companies continues to evolve, companies must concurrently explore consumer-side identity technologies like CIAM or Know Your Customer (KYC). Beyond establishing the supporting processes for onboarding new employees / credentialing required access and provisioning any necessary accounts and offboarding of no-longer-required accounts, organizations should start to identify the specific accounts that require privileged access. This often will include system and network administrators, incident responders, other sensitive or intellectual property-related accounts, APIs, and system accounts.
Privileged Access Management (PAM)
Once this landscape is sufficiently understood, organizations can move to incorporate privileged access management (PAM) by vaulting all system account passwords and incorporating additional logging and access controls for more privileged user accounts. Industry leaders such as Delinea (formerly Thycotic) or CyberArk both cite the importance of both having awareness and reducing overly permissive accounts as a core tenet of ZTA. As a result, throughout the “Know what is” discovery phase and the “Only keep what is needed” phases, companies should look to remove any overly permissive accounts and ensure any unneeded legacy accounts or previously sunset APIs are no longer valid. A recent example of why eliminating these no-longer-required vectors was uncovered by the Jscrambler research team in their blog post related to a new batch of web skimming attacks.
This effort could be as simple as limiting most accounts to be leveraged for lateral movement via instituting a group policy object (GPO) policy that default executes PowerShell / VBS / WScript / Json scripts in Notepad. Another GPO-based improvement to make almost immediately is to block the ability to mount iso files within the environment. In a related post written by an RH-ISAC Core Member employee, “ProgrammaticAccessOnly” needs to be added to HKEY_CLASSES_ROOT\Windows.IsoFile/shell/mount as a Reg_SZ. Historically, monitoring or controlling ISO mounting has always been a challenge, and the beautiful thing about this proposed solution is that all accounts are protected. At the same time, administrators can still mount drives via PowerShell & the Mount-DiskImage command.
Role-Based Access Control (RBAC):
As a program matures, it is natural for standard user profiles to be defined, enabling more granular access control options such as role-based access control (RBAC). Leveraging RBAC-style profiling can assist with identifying the highest-risk accounts and can, if properly implemented, significantly reduce the quantity of overly permissive accounts if properly designed and implemented.
Just-in-Time Provisioning (JiT):
Once RBAC is successfully in place, organizations can carefully explore implementing just-in-time (JiT) provisioning, zero-trust access being implemented in the truest form. JiT is, in a nutshell, the process of automating dynamic access policies. Typically, this is based on RBAC profiles, and the only significant improvement is that no account retains any access to any network-connected resources indefinitely ever. Instead, access is provisioned at the time of need for the specific resource/asset needed for the specific window of time the type of access is needed. Then, post-activity, all access is dynamically revoked until the next time an authorized party requests access. JiT significantly improves an organization’s security posture in terms of permissive access by further limiting the impact of an account compromise by only providing an absolute base level of access to any account at any given moment and only for the specific resource actively in use at the time.
Often organizations exploring JiT are simultaneously exploring (if not already implemented) some form of user entity and behavior analytics (UEBA) solution to perform complex anomaly detection – ideally global, contextual, as well as collective at scale.
Have questions about zero trust? RH-ISAC’s Member Exchange is the home for discussions among retail and hospitality peers. Not a member? Learn how becoming a part of the RH-ISAC community could benefit you.