The stakes remained high for retailers this holiday season, with attackers aggressively focusing their attention on the commerce sector – both in the U.S. and abroad. Several factors played into the increase in malicious activity — the surge in online traffic due to pandemic-related restrictions as well as compounding supply chain issues and associated inventory shortages — creating a perfect storm for cyber criminals intent on disrupting a retailer’s “make or break it” time of year.
With the pressure rising, it came as no surprise that Akamai witnessed an uptick in a variety of attack methods and vectors. From credential stuffing and account takeover (ATO) attacks unleashed by malicious bot operators, to Log4j exploitation attempts and WAF assaults, the past few months and into 2022 have been all about bad actors setting their sights and pointing their tools at Commerce players.
If we take a quick look back at 2021 across all industries tracked by Akamai, the commerce vertical led overall bot growth for the year (up 41% since April 2021), beating out other highly targeted verticals like video media and high technology.
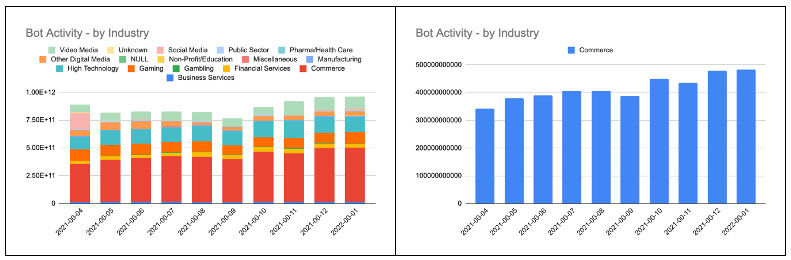
Looking deeper within the Akamai commerce sector, the retail subvertical showed bot traffic gains while hotel & travel subvertical traffic remained relatively flat. It’s important to note that most of the increases were from bots categorized as malicious vs. benign.
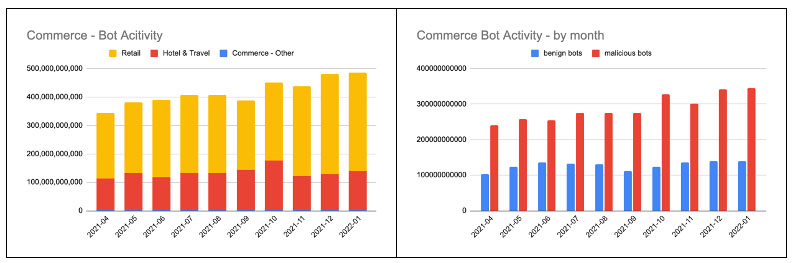
The increase in malicious bot activity for commerce makes sense for several reasons, as bot operators looked to grab limited inventory (as soon as hot items were released or replenished) ahead of actual customers in order to resell it at higher prices on other online marketplaces.
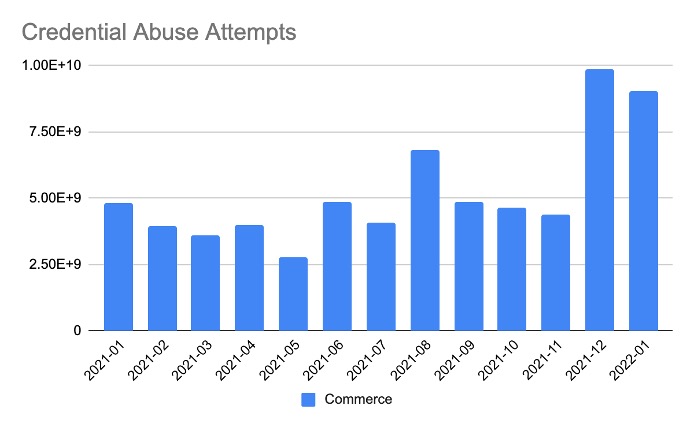
Automated bots were also busy testing combo-lists of stolen credentials, part of the early stages of the ATO cyberattack kill chain designed to steal reward points and cash out on a retailer’s hard-earned brand loyalty. From November into December, Akamai data reflects a 226% increase in credential stuffing attempts as attackers aimed to compromise customer accounts, with the trend carrying over into January 2022.
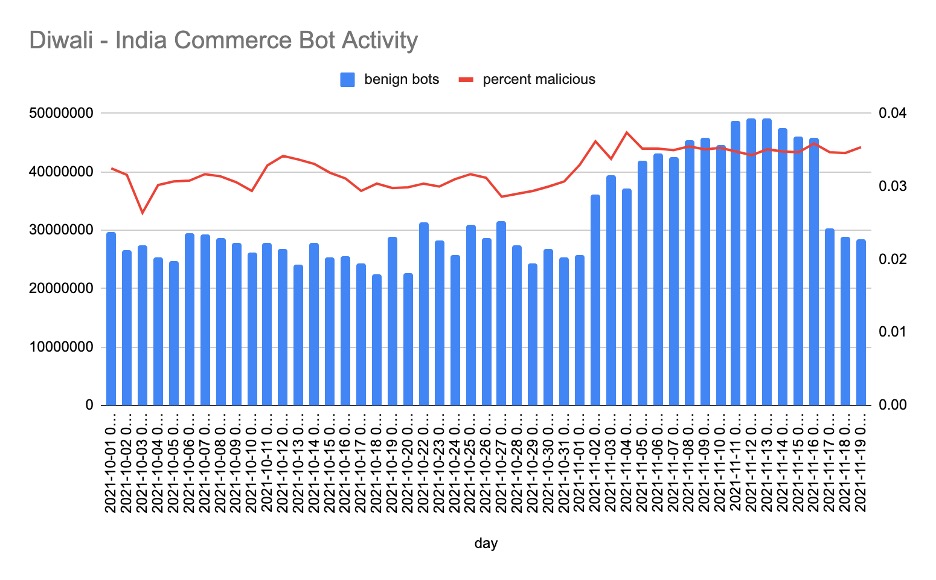
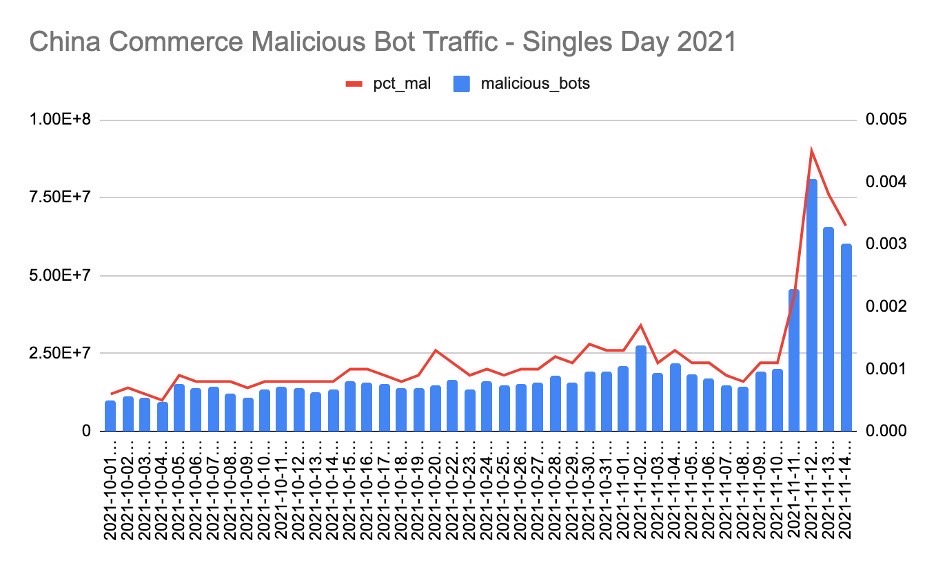
Bad bot activity was especially evident with the onset of mega-online shopping holidays across the globe. For India’s Diwali and China’s Singles Day, Akamai witnessed significant jumps in malicious bot activity — more than 55% during the Diwali celebration — and bots showing up in full force for China’s biggest shopping day of the year.
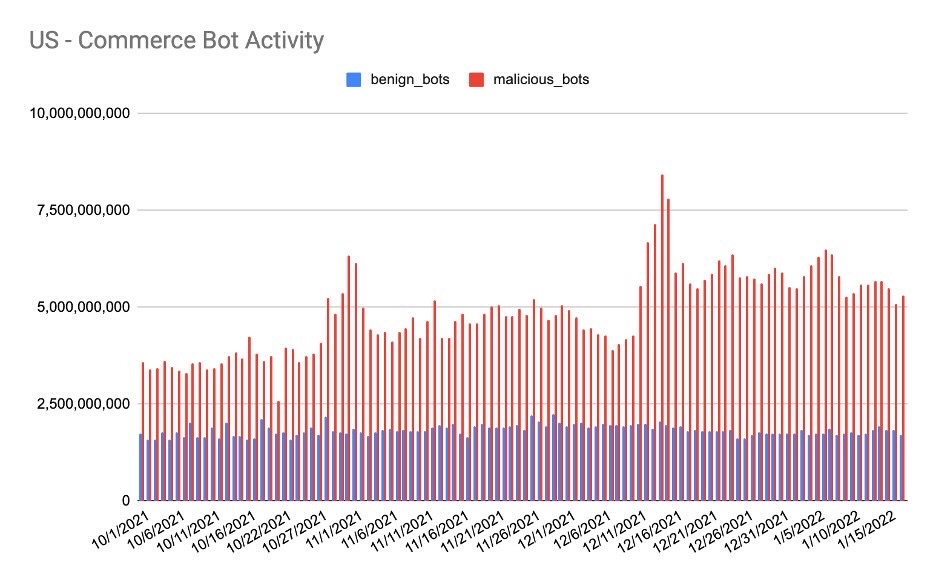
The U.S. also experienced a steady increase in malicious bots, aligning with the push for consumers to begin the holiday shopping season early with heavy promotional activity starting as early as October. It’s clear that when holiday inventory showed up, so did the bots. The consistent surge continued through Christmas and into the New Year, aligning with the NRF’s estimate that 65% of U.S. consumers planned to continue shopping the week after Christmas – possibly contributing to the sustained levels of malicious activity we observed in January.
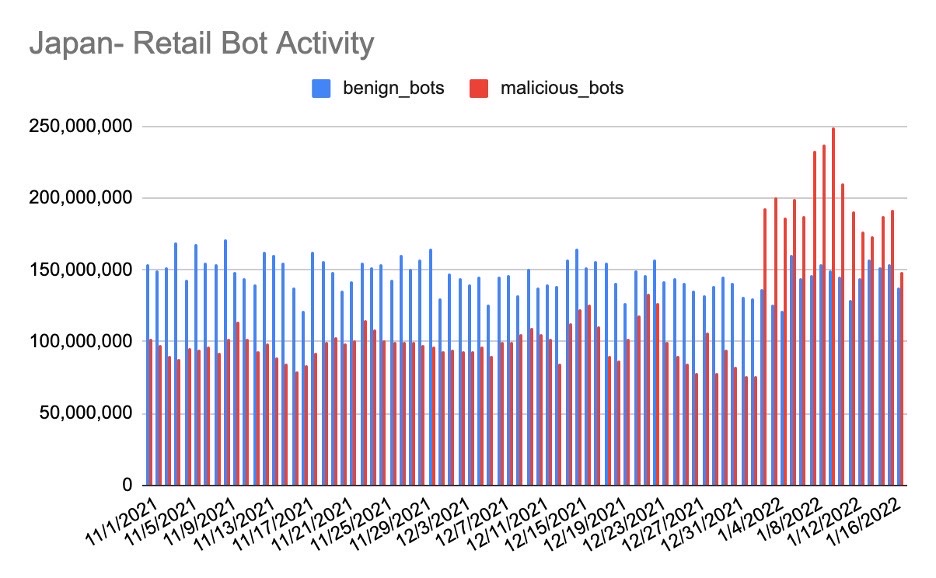
Early New Year bot attacks also were evident in Japan during the annual Hatsu-uri and Fukubukuro shopping sales, resulting in a ~242% jump in bad bots targeting retail-focused organizations.
The bottom line for bots — it’s clear that operators are highly motivated to target the commerce sector, requiring retail organizations to have the right defenses in place to prevent business and brand-impacting disruptions, not only throughout the holiday season but for other high-heat events as well.
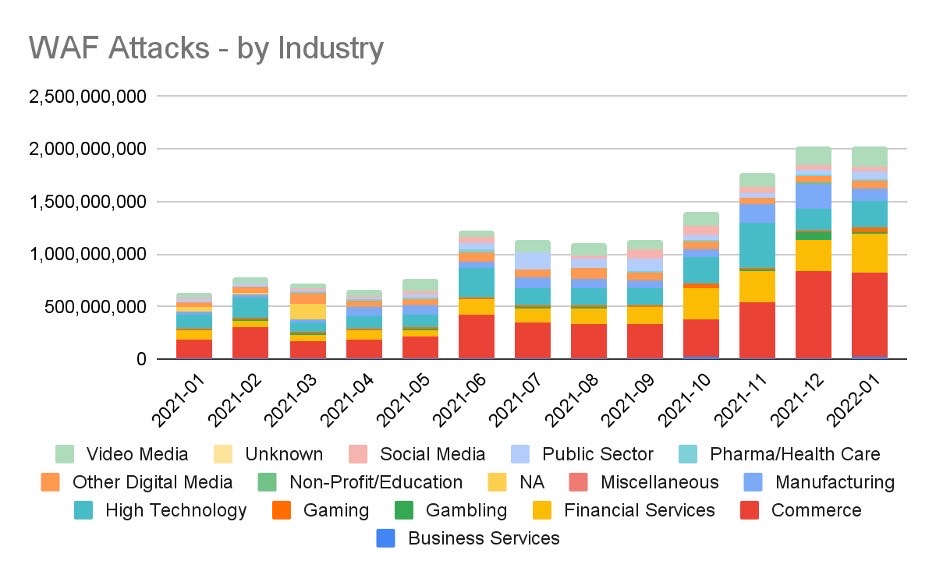
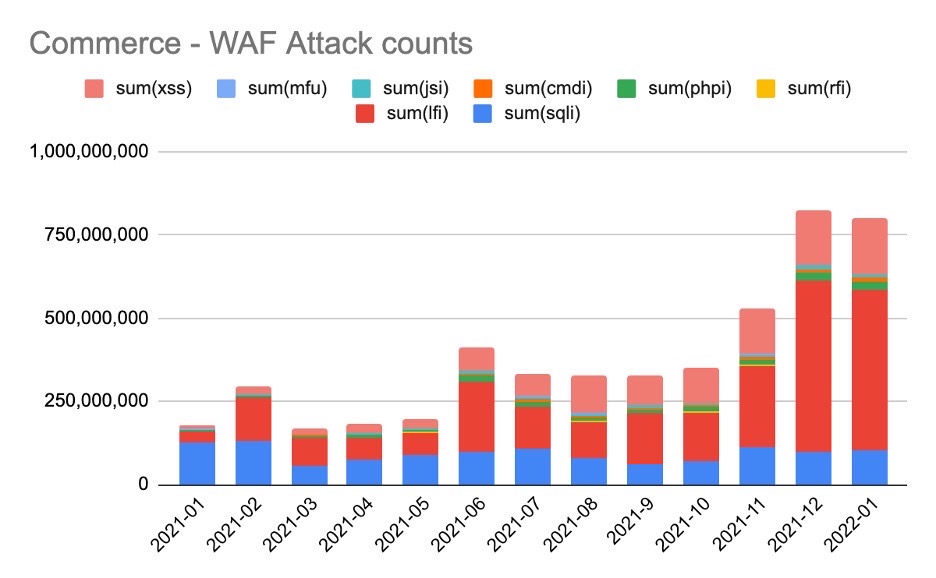
However, the same holds true for other types of attacks that were heavily focused on commerce during both the holidays and into the new year as well. Based on our data, the commerce vertical experienced a significant uptick in WAF attacks, jumping 30% from November into December. Going back to early 2021, commerce WAF three-month average activity is up 3.35x.
Digging deeper into the various types of attack vectors, we see a spike in cross-site scripting (XSS) and local file inclusion (LFI) attacks. The former aims to inject malicious scripts into trusted webpages to be executed by the browser, while the latter attempts to trick a web application into exposing files on a web server in an attempt to extract sensitive data. For example, with XSS, attackers target authentication data, such as usernames, passwords, and cookie data, that can be used to manipulate the user’s session or even log in to the legitimate user’s account. Next, the attacker could use this information to take over the account, placing fraudulent orders or changing shipping addresses to receive goods paid for by the real owner’s credit card.
In addition to seeing a tremendous jump in WAF attacks, retailers had to contend with the public disclosure of the Apache Log4j (CVE-2021-44228), a critical remote code-execution and data exfiltration vulnerability that impacted organizations across all industries globally. Based on Akamai data that tracked Log4j exploitation attempts per hour, attackers were eager to take advantage of the exploit against retailers in particular, when security teams were already stretched thin and strained during December’s holiday frenzy.
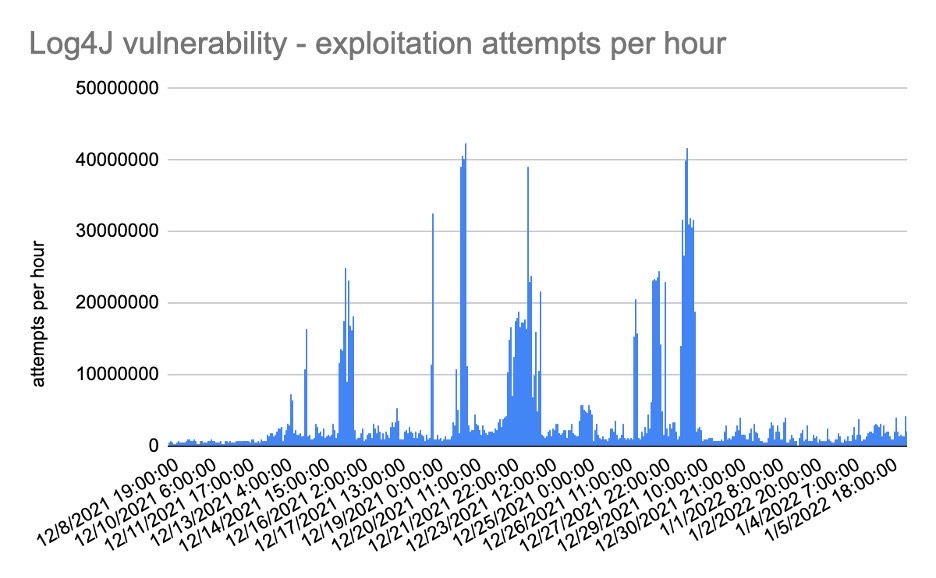
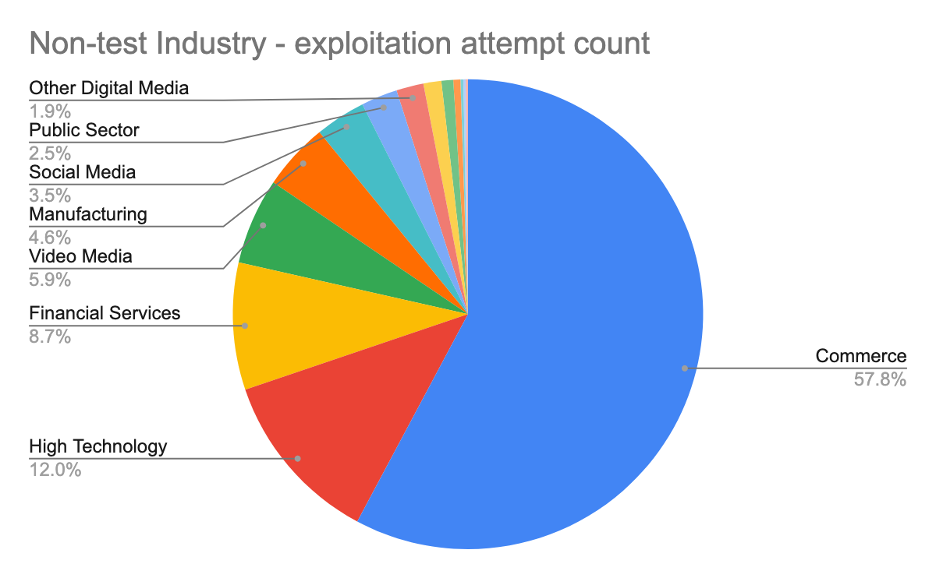
In fact, commerce was the most heavily targeted sector accounting for ~58% of all Akamai observed Log4j attempts. And as an important note, Akamai worked swiftly to provide recommendations for Log4j mitigation for our customers. With any zero-day exploit, patching all impacted applications and systems as quickly as possible is critical to help reduce attack surfaces and damage from potential compromise.
Top of Mind Security Considerations for 2022
Bad actors have already proven to be highly focused on disrupting the commerce sector with no signs yet of letting up. So what does that mean concerning an organization’s security posture investments and priorities as we move through 2022?
Because the COVID-19 pandemic continues to drive accelerated — and sometimes rushed — digital transformation initiatives for organizations globally, cybercriminals will remain intent on discovering and exploiting defensive gaps. In fact, 32% of retailers admitted to rolling out new tech without the typical rigor and security safeguards in place in order to capture more sales during the pandemic. As a result and based on Akamai’s observations, retailers will contend with highly motivated threat actors intent on compromising web properties, monetizing digital assets, disrupting internet-facing infrastructure, and stealing customer data via a variety of attack vectors and methods.
In the wake of increasing malicious bot activity and WAF-directed attacks, commerce organizations must have the right security controls in place to help reduce risk and attack surfaces alike. But defensive solutions must balance the need for more robust security with the need to run the business — without turning off customers. As part of the fallout from the pandemic, consumers became less loyal to brands as products became more difficult to find, with 46% percent of U.S. consumers switching brands or retailers.
Therefore, improving customer experience and removing friction from the path to purchase — via tech enhancements — to retain and attract customers has become a top priority over the past year, and will remain a strategic area of investment for the foreseeable future. The same applies to security investments. In today’s volatile retail environment and with CX top of mind, security solutions must also remove operational and management friction while enabling more seamless digital experiences so retailers can better compete for customer loyalty.
This also speaks to the need for collaborative security decisions. Marketing and CX teams should consult security before launching new solutions to discuss the potential impact of existing defensive solutions — like bot management — on proposed changes. On the flip side, security teams should be comfortable bringing CX, marketing, and loss prevention stakeholders into evaluations of new security investments. At the end of the day, security must be at the forefront of brand-impacting technology decisions, and not an afterthought, in order to optimize the customer journey and better mitigate risk.



