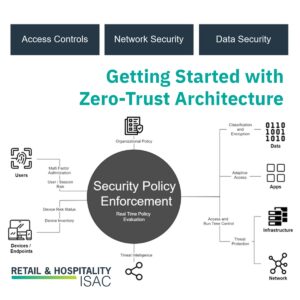
Zero-Trust Architecture (ZTA): How to Get Started
Now that we have it defined, how do we practically approach the path to zero-trust architecture (ZTA) and why does it matter? Suppose we start the ZTA discussion by agreeing on a standard definition in its simplest form, i.e., limiting the impact of any unauthorized events by design. Many current industry definitions summarize the key…
Read More